How to Compare Cloud Security Tools: The Evaluation Framework
Key Insights Introduction You’re not struggling to find cloud security tools. You’re struggling to compare...

Apr 29, 2025
The recent news about Google’s multi-billion-dollar acquisition of Wiz has sparked widespread conversation across the cybersecurity world. Its price tag reflects its strong reputation, Wiz is a leader in Cloud Security Posture Management (CSPM) solution. Its strength lies in identifying potential risks before they impact your live environment.
However, as with many high-profile acquisitions in cybersecurity, this move is prompting security leaders to reassess their vendor relationships and long-term strategies. In the short term, Wiz’s core CSPM capabilities are unlikely to be affected, it’s a mature offering with proven value. But when it comes to Wiz Defend, their newly launched, early-stage runtime security product, the outlook is less clear. Lacking many of the advanced features required for robust cloud workload protection, its development trajectory could be impacted or deprioritized, leaving organizations in need of deeper runtime visibility and response capabilities looking elsewhere.
At ARMO, we believe that robust runtime defense isn’t just an added benefit, it’s a fundamental necessity for modern cloud security. That’s why we developed ARMO CADR (Cloud and Application Detection and Response), the first cloud security solution driven by explainability. ARMO CADR connects the dots between your code, runtime behavior, cloud infrastructure activity and even your accepted risks, to reduce the burden on SecOps and SOC teams.
In this post, we’ll explore the crucial differences between ARMO and Wiz, in cloud runtime security. We’ll demonstrate why real-time visibility is rapidly becoming an indispensable component of any comprehensive cloud security strategy.
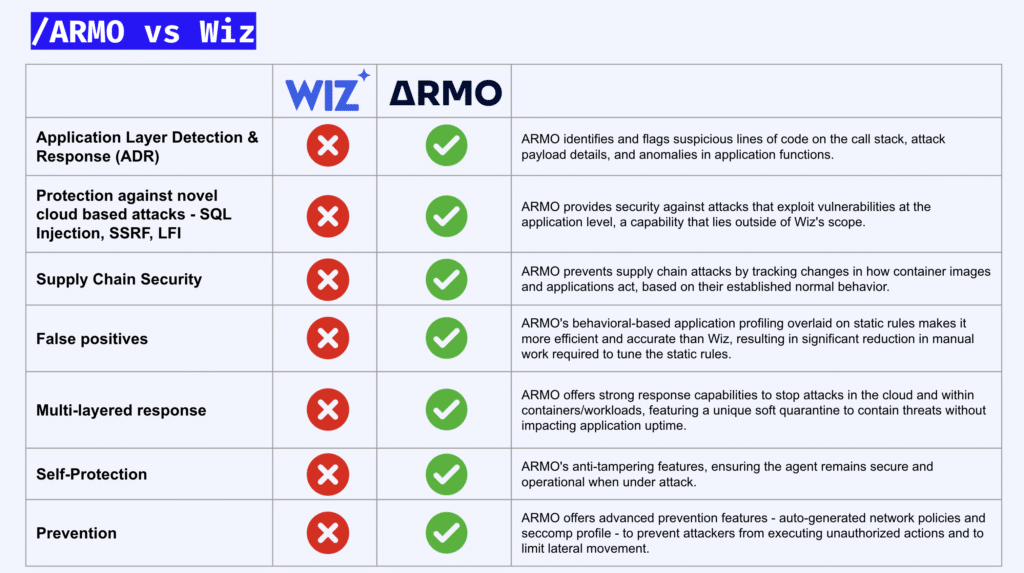
ARMO CADR offers a comprehensive view of security threats that is truly unique. It correlates high-level cloud activity with granular, often subtle, suspicious application behavior. This deep connection empowers SecOps teams to rapidly trace the complete attack stories, amplifying genuine threat signals and effectively filtering out noise. The result? Measurable improvements in both Mean Time To Detect (MTTD) and Mean Time To Respond (MTTR).
Wiz specializes in cloud security posture management, providing an agentless solution that’s widely used to identify and remediate misconfigurations across cloud environments. This approach forms a vital initial layer of defense.
However, the reality is that some risks are consciously accepted due to prioritization, business constraints, or incomplete initial context. Other threats may simply evade static analysis or be misjudged during the triage process.
It’s also important to distinguish between theoretical risk – based on best practices, compliance checks, and known security guidelines and runtime risk, which reflects the actual behavior of real workloads running in real infrastructure, under real-world conditions. Which is the divide between the concepts that guide hardening and compliance and runtime security.
Once code is running in a production environment, both new and previously overlooked threats can emerge. This is precisely where a strong runtime security layer becomes critical. It provides the essential visibility and defense mechanisms to detect and respond to real-world attacks as they happen.
Let’s examine how ARMO and Wiz address three common application-layer threats in a live environment:
Runtime protection is key to identifying and mitigating supply chain compromises, as highlighted by incidents like the Kong Ingress Controller vulnerability in January 2025 and the GitHub tj-actions leak.
Security teams are often overwhelmed by a barrage of alerts. ARMO CADR addresses this challenge by combining static detection rules with intelligent behavioral profiling. This approach effectively filters out irrelevant alerts and surfaces high-confidence threats, even those that don’t match pre-existing rules, such as zero-day exploits. This significantly reduces the need for manual rule tuning and improves the signal-to-noise ratio.
In contrast, Wiz primarily relies on static rules, often requiring significant environment-specific tuning. While they offer support for custom runtime detection rules, the ongoing maintenance of these rules can be resource-intensive and may still miss novel attack vectors.
ARMO provides a range of granular response options, from revoking compromised IAM roles and blocking unauthorized S3 bucket access to quarantining suspicious containers.
Our innovative “soft quarantine” feature offers a significant advantage: it isolates a potentially malicious process with strict seccomp and network controls while allowing the application to continue running. This minimizes disruption to production environments, a critical consideration for maintaining business continuity.
While Wiz offers automated runtime response policies, their primary response mechanism is often hard shutdown. This approach carries the risk of disrupting application availability and can lead to negative consequences such as data loss and file system corruption.
ARMO’s agent is engineered with anti-tampering protections, ensuring it cannot be easily modified or disabled by attackers. While both ARMO and Wiz leverage eBPF for deep telemetry collection, ARMO prioritizes the security and operational integrity of its agent, even under active attack.
ARMO’s recent publication of the Curing rootkit demonstrates how many security vendors of Wiz’s caliber utilize eBPF superficially, without fully understanding and addressing its inherent blind spots. This highlights ARMO’s deep understanding and informed implementation of eBPF for runtime security.
Wiz stands out as an excellent CSPM and shift-left security tool. However, its entry into the field of runtime protection is more recent, and its capabilities in this critical area still lag behind dedicated cloud runtime protection solutions. ARMO CADR, on the other hand, is purpose-built for cloud-native runtime defense, providing security teams with the comprehensive visibility, rich context, and granular control necessary to effectively stop modern attacks in their tracks.
If you are serious about safeguarding your cloud workloads at every stage of their lifecycle – from the initial build process all the way through to runtime – ARMO is the clear choice for comprehensive and effective protection.
Need help presenting your case? Download this slide and add it to your pitch deck 👇

Key Insights Introduction You’re not struggling to find cloud security tools. You’re struggling to compare...

Key Insights What is the best eBPF security tool for Kubernetes? For detection-only, Falco. For...

Key Insights What are the three types of cloud compliance tools? Audit-prep platforms (Drata, Vanta)...