Cloud Security’s Unspoken Truth
Why most security findings are noise and and how to focus on what actually matters?...

Mar 9, 2023
ARMO Platform has added the CIS EKS benchmark. Now, with Amazon Elastic Kubernetes Service (EKS) users can add this specific benchmark to the frameworks already available to them.
In recent years, Kubernetes has become the de facto standard for container orchestration. As a result, many organizations have turned to Kubernetes to help them modernize their IT infrastructure and improve their application deployment processes. Amazon’s Elastic Kubernetes Service (EKS) is one of the most popular ways to deploy Kubernetes clusters in the cloud. It offers a managed service that makes it easy for organizations to run Kubernetes at scale.
The shared responsibility model from AWS means that users are accountable for their EKS cluster’s security. This is where solutions like ARMO Platform can be of great help. Currently, ARMO Platform supports three industry-recognized frameworks out of the box. The list includes the general Kubernetes CIS Benchmark. However, to better serve EKS users, ARMO recently introduced support for the EKS-specific variant of the CIS benchmark. With it, as an EKS user, you can better identify security compliance gaps. You can analyze the root cause for security misconfigurations, and fix them with assisted remediations. All this, while monitoring for drifts.
While the General Kubernetes CIS Benchmark covers all aspects of securing your Kubernetes infrastructure, the ones for managed Kubernetes distributions are much abbreviated. This is thanks to the fact that many of the security aspects are covered by the service provider.
That said, you cannot be lulled into a false sense of security by this. According to the CIS AKS Benchmark: “AWS is responsible for protecting the infrastructure that runs AWS services in the AWS Cloud. For Amazon EKS, AWS is responsible for the Kubernetes control plane, which includes the control plane nodes and etcd database.” In the graphic below, you can see where AWS draws the line for the users of EKS.
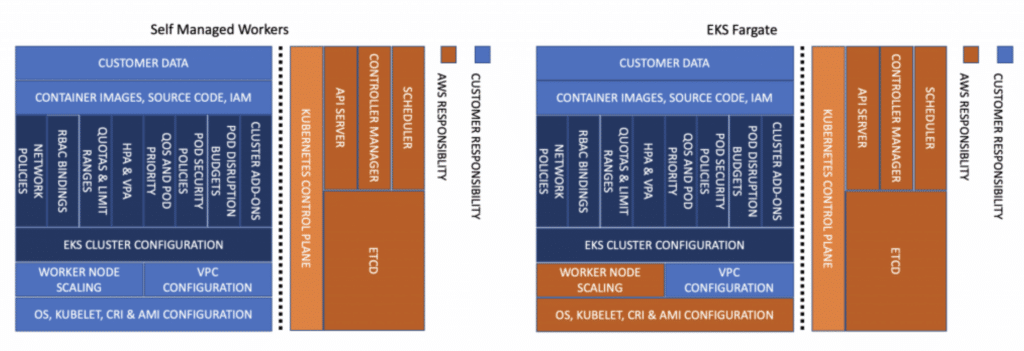
The EKS CIS Benchmark covers five subsections. Please note the numbering follows the benchmark numbering, which is why it starts at (2):
ARMO’s mission is to keep DevOps engineers security aware, without adding to their burden. To that end we add layers of security in an automated fashion to the tools in the DevOps stack. The Kubernetes CIS Benchmark is helpful and relevant to EKS users.
However, by introducing the EKS-specific CIS Benchmark, engineers have an option that caters specifically to their needs. Not only does it offer remediations for manifests you deployed to the cluster, but also to the cluster itself using the aws eks command line tool or the EKS console. These are also places you can get your results.
ARMO CIS EKS controls scan all of the categories mentioned above. This gives users the most comprehensive solution for EKS benchmarking available to date. To this end, ARMO developed custom controls, or mapped existing controls to the CIS EKS benchmark. To date, ARMO Platform supports 50 of the applicable 53 controls. They can be found in the Kubescape library of controls. This option is currently the largest number of out of the box controls available for EKS users.
The CIS EKS benchmark is also available to Kubescape users and can be used either directly from the CLI or can be integrated into different CI/CD tools (e.g IDE, Jenkins, ArgoCD, Github, etc.)
In case you are new to ARMO Platform you can get a guided tour here.
For more experienced users of ARMO Platform (or after viewing the video above) read on to learn about what we added for you.
The first step is to make sure you have the most up to date Helm chart installed. Then you can go to the ARMO Platform UI, or use this functionality with the ARMO or Kubescape CLI, in addition to the many plug-ins and extensions available for the DevOps stack.
From this step on, for the purposes of illustration, we will be showing the ARMO Platform UI.
Upon selection of an EKS cluster and the CIS-EKS framework, you get the list of tested and failed controls rolled up, per framework subsection.
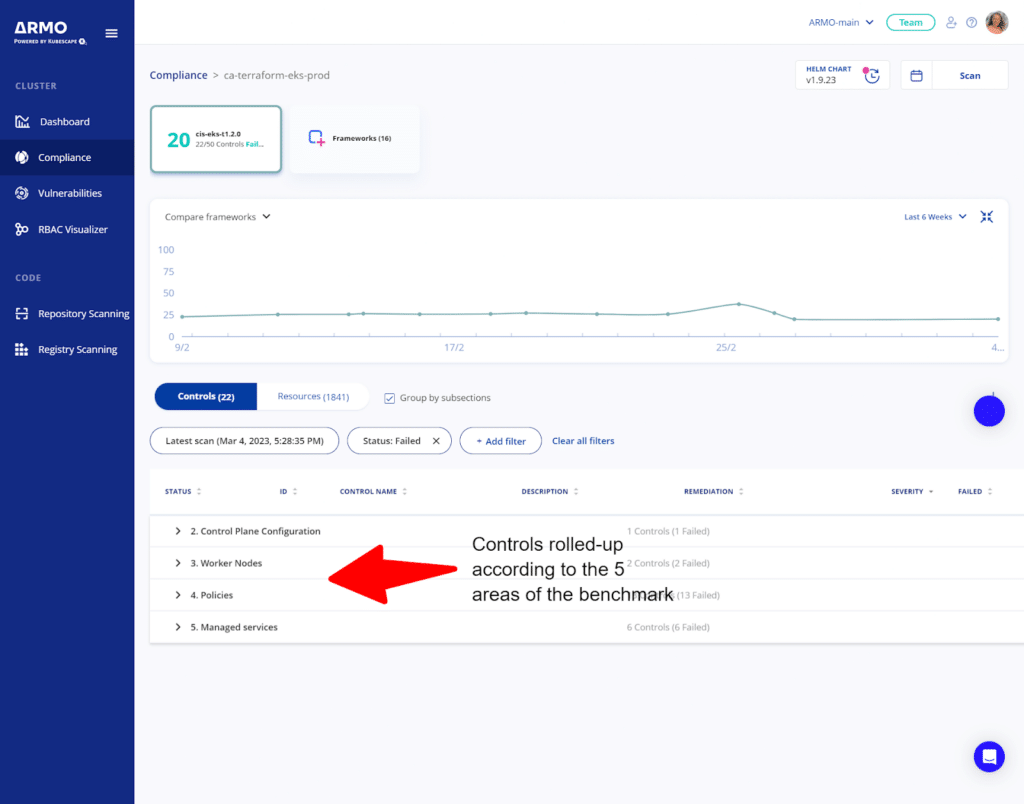
For more information, you can expand a particular subsection, to learn more about the controls that failed.
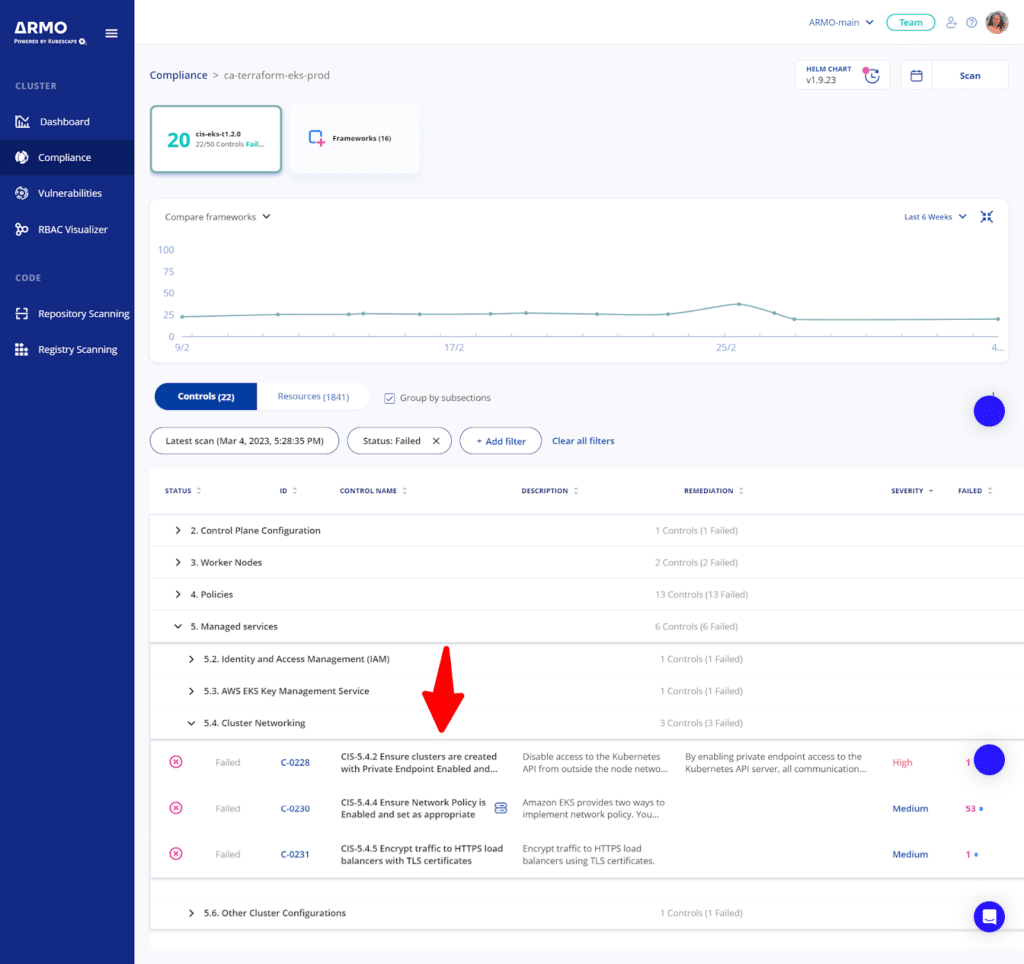
As ever, assisted remediation is at your fingertips, and can be accessed in the same way as you always use ARMO Platform.
Please note that this is an example implementation in ARMO Platform UI. As mentioned above, you can get your results via all available ARMO and Kubescape integrations with the addition of the AWS CLI and console.
Support for the CIS EKS Benchmark builds on the CIS compliance journey that ARMO started a few months ago. It is a useful and specific add-on to the existing support for CIS Kubernetes V1.23.
Upcoming releases will include support for the CIS AKS (Azure Kubernetes Service) and CIS GKE (Google Kubernetes Engine) frameworks. We will, of-course, be updating existing frameworks and controls according to new benchmark versions, as they roll out.
This new feature enables ARMO Platform to better help AWS EKS users maintain their cluster’s security posture and ensure compliance with industry standards.
If you are an EKS user that is finding the signal to noise ratio hard to deal with, when testing against the general Kubernetes CIS benchmark. If you are finding the findings of the EKS CIS benchmarking tool you are using today, not substantial enough, give ARMO Platform a try.
Why most security findings are noise and and how to focus on what actually matters?...

We’ve been busy! Our latest summer updates introduce powerful new capabilities to help you detect,...
Let’s be honest. Most cloud security alerts feel like trying to read a book with...