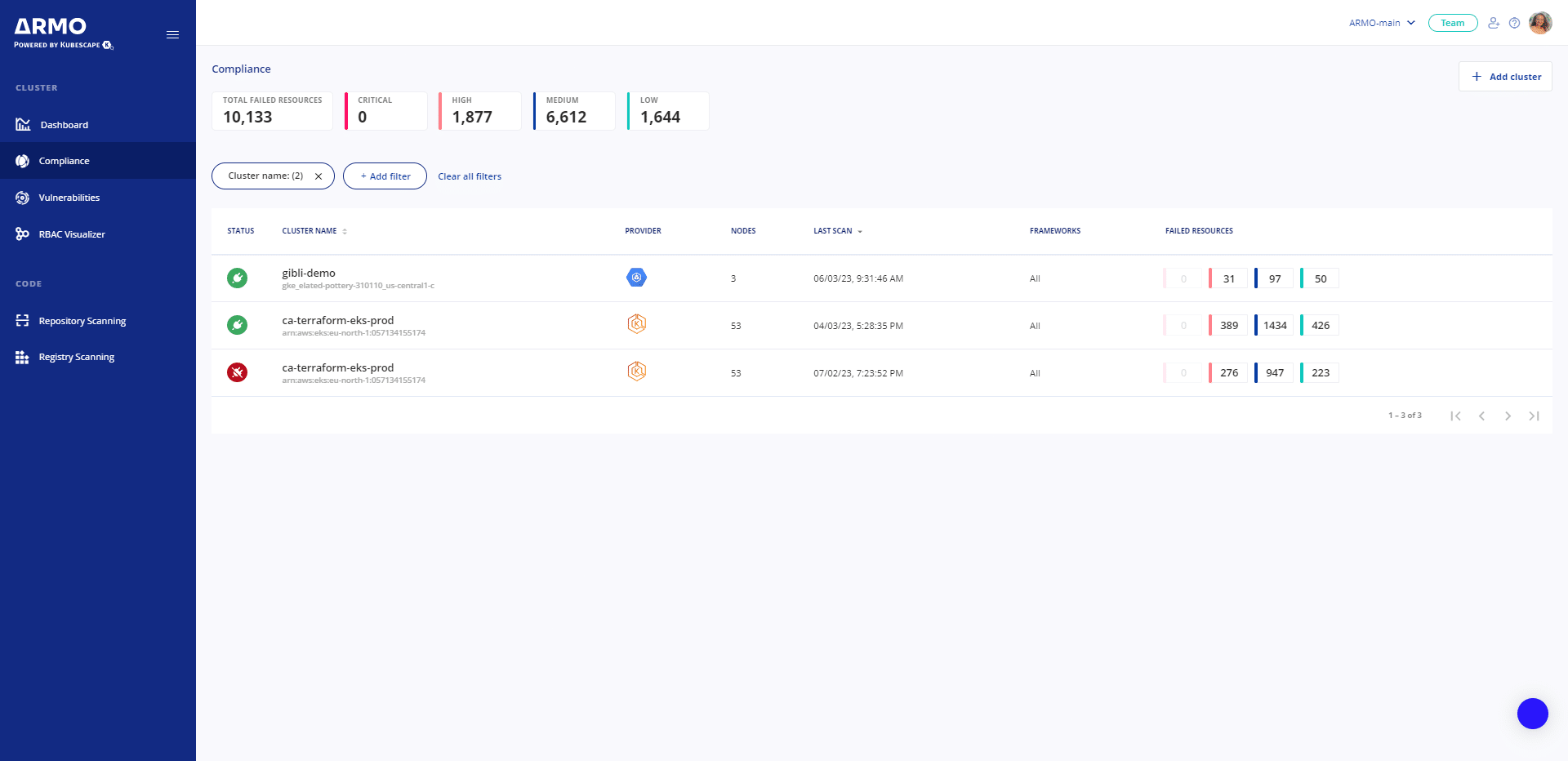
What is Kubernetes hardening?
Kubernetes hardening involves security measures taken to harden Kubernetes clusters. This practice secures the parts of the Kubernetes architecture (e.g. the control plane, worker nodes, or containerized services) that can have flaws and incorrect configurations. If not acted on, these loopholes can be exploited by threat actors with malicious intent.
Kubernetes hardening options
There are numerous frameworks that provide / outline recommendations about hardening. This can involve a lot of manual work, or using a collection of specialized tools. In any case, you do not get the coveted “big picture”. None of these options is ideal due to the toil associated with getting the job done.