ARMO Now Supports GKE Autopilot Clusters 🎉
We’re excited to announce that ARMO now fully supports Google Kubernetes Engine (GKE) Autopilot clusters!...

Mar 7, 2024
In the ever-changing world of Kubernetes security, it’s crucial to stay ahead of threats while maintaining operational efficiency. That’s why we’re excited to introduce our latest feature: Auto-Generated Kubernetes Network Policy, based on application runtime behavior, powered by eBPF (extended Berkeley Packet Filter) technology. With this addition, organizations can easily apply native Kubernetes network rules without worrying about disrupting their production systems.
Addressing these challenges requires a combination of careful planning, robust tooling, and continuous monitoring to ensure that Kubernetes network policies effectively balance security and operational requirements.
As organizations embrace cloud-native architectures and Kubernetes for container orchestration, ensuring robust network security becomes increasingly hard. Manual creation and management of Kubernetes network policies can be time-consuming and error-prone, often leading to misconfigurations and security gaps. Our new feature addresses these challenges by automating the generation of network policies based on workload behavior, leveraging the power of eBPF to provide insights and enable the control you need.
ARMO Platform’s auto-generated Kubernetes network policy feature analyzes workload behavior and communication patterns within the Kubernetes cluster. Based on this analysis, it automatically generates network policies to regulate traffic flows between pods and services. Whether it’s enforcing segmentation, access control, or traffic encryption, ARMO Platform adapts dynamically to the evolving needs of the environment.
Generating Network policy involves five steps, as described in the following sections:
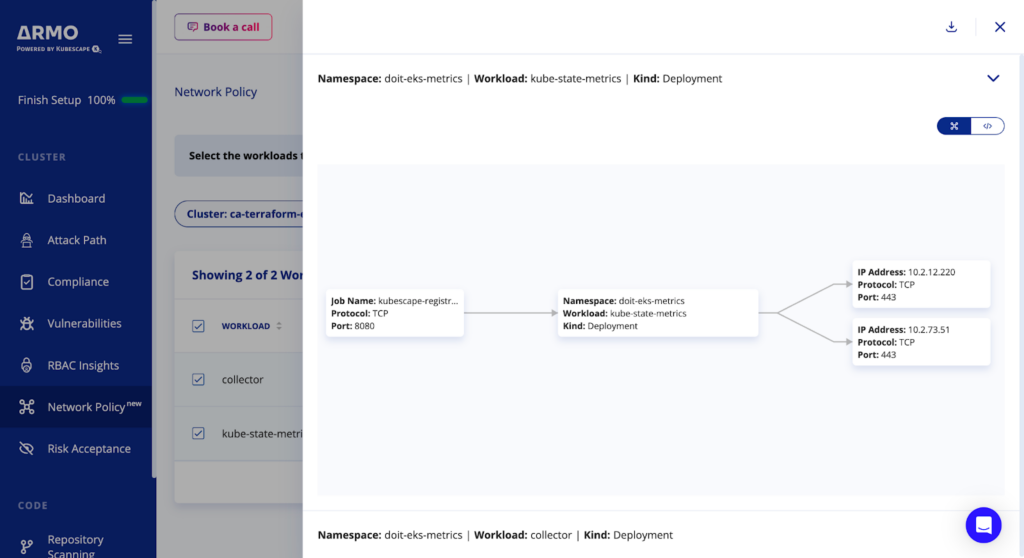
Use the graph view to visually validate if this is the policy you want, or if something should be changed.
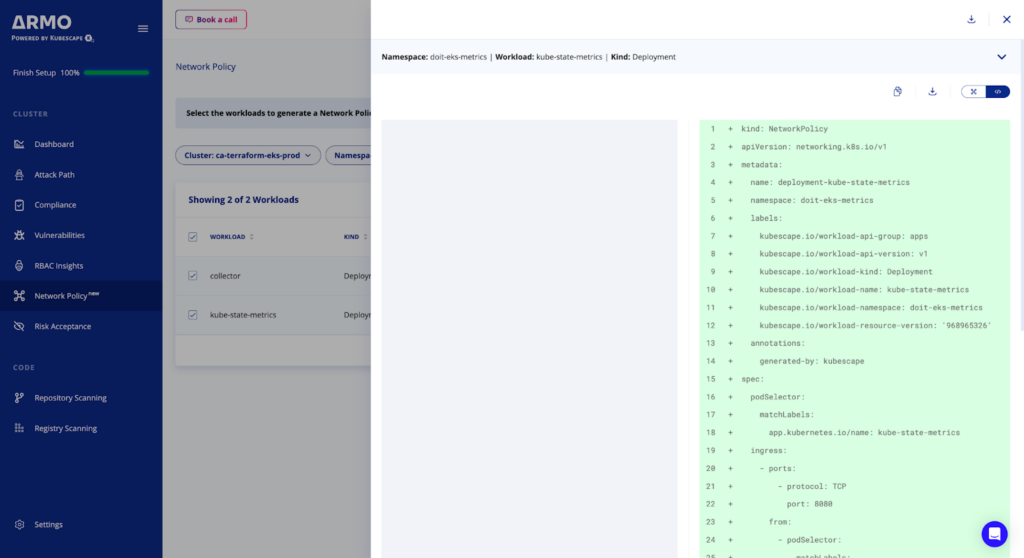
Toggle on the code View to see the raw YAML output of the network policy recommended for that workload.
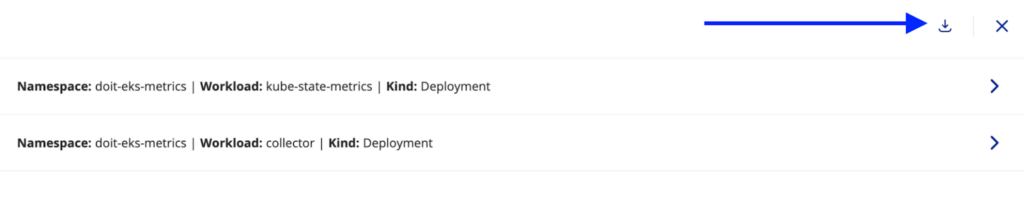
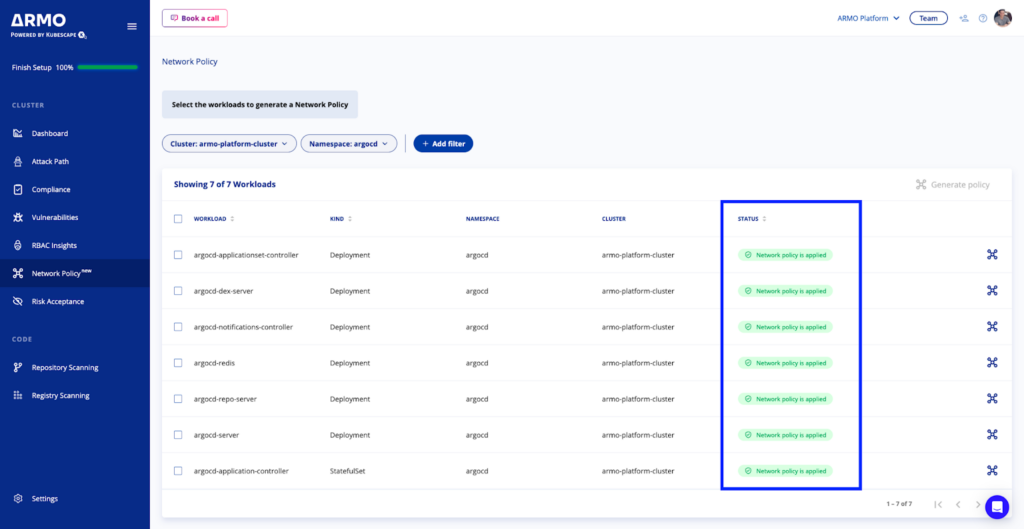
After reviewing the generated network policies, click on the Download button to download all the policies, or you can select to download the selected policy:
Once you’ve applied the network policy, ARMO Platform identifies, and updates the status automatically to ‘Network policy is applied’
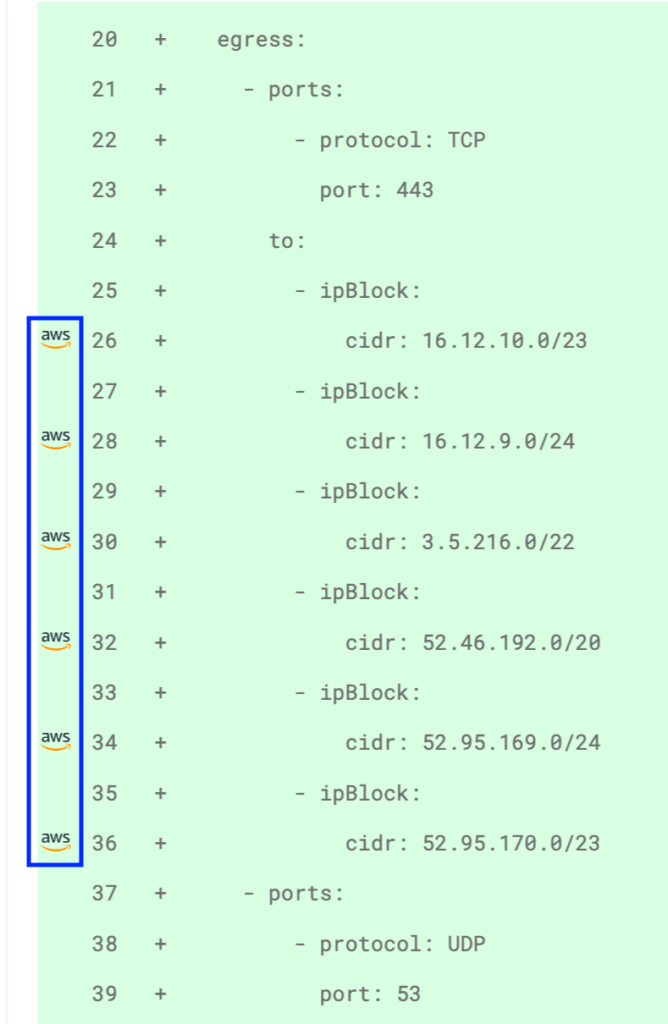
Highlights the CIDR range an IP address belongs to (e.g. a cloud provider) enabling efficient routing and defining firewalls based on CIDR ranges.
Looking ahead, we’re committed to enhancing the ARMO Platform’s network policy capabilities by adding support for additional CNIs such as Calico, Cilium, and Istio. By extending compatibility with these popular networking solutions, we aim to bring all network policy generation and maintenance to one, security-aware, place.
It’s important to keep Kubernetes environments protected from threats. ARMO Platform’s Auto-Generated Kubernetes Network Policy feature, powered by eBPF technology, offers unique automation, efficiency, and control. With this innovative solution, organizations can achieve seamless security without compromising operational agility, empowering them to confidently embrace cloud-native architectures.
Experience the future of Kubernetes security with our auto-generated network policy feature. Get started today and unlock a new level of protection for your containerized workloads.

The only runtime-driven, open-source first, cloud security platform:
Continuously minimizes cloud attack surface
Secures your registries, clusters and images
Protects your on-prem and cloud workloads

We’re excited to announce that ARMO now fully supports Google Kubernetes Engine (GKE) Autopilot clusters!...

Software supply chain attacks cost businesses $45.8 billion globally in 2023 alone, and is projected...

Imagine this situation: you recently updated one of your infrastructure software components. A few weeks...