ARMO Now Supports GKE Autopilot Clusters 🎉
We’re excited to announce that ARMO now fully supports Google Kubernetes Engine (GKE) Autopilot clusters!...

Aug 15, 2024
Runtime anomaly detection is fast becoming a critical component for protecting containerized environments. Recent advancements in this field are addressing long-standing challenges and introducing innovative approaches to enhance security posture.
Runtime detection tools often face a significant challenge: generating too many false positives. This leads to two major problems – alert fatigue among security teams and difficulty in identifying real threats. The root cause of this issue lies in the use of generic rule sets that aren’t customized for specific workloads.
The lack of context in these generic rules is a fundamental issue. Traditional security approaches rely heavily on known patterns and industry best practices. While these practices are valuable, they often fail to account for the unique needs of actual production workloads. This oversight is critical because applications vary widely in their design and functionality. Each application has its own specific requirements and behaviors. This diversity is not just a technical necessity but also a key factor in business innovation and differentiation.
Therefore, a one-size-fits-all approach to security rules is inherently flawed when dealing with the complex and varied landscape of modern applications.
To address these challenges, ARMO has developed a novel method of runtime anomaly, incorporating several key components:
1. Application Profiling: Utilizing eBPF technology, detailed profiles of applications are created, capturing information on processes, file activity, system calls, permissions, and network activity.
2. Contextual Learning: The system observes normal behavior patterns over a customizable learning period (typically 24 hours) to establish a baseline for each application.
3. Anomaly Detection: Once profiles are established, the system can detect deviations from the learned behavior, significantly reducing false positives.
4. Behavioral Inspection: In addition to anomaly detection, custom rules are incorporated to identify specific attack patterns, such as reverse shells or in-memory execution.
– Reduced False Positives: By learning the expected behavior of applications, the system minimizes alerts for legitimate activities.
– Zero Configuration: The tool automatically starts learning the environment upon installation, requiring minimal setup.
– Improved Security Posture: Anomaly-based detection makes it challenging for attackers to bypass security measures.
– Flexible Alert Integration: Support for various output formats, including AlertManager, HTTP, and syslog, allows for easy integration with existing security workflows.
Modern implementations of this approach can be deployed using GitOps practices with tools like Flux or ArgoCD allowing for easy reproducibility across multi-cloud environments. This method enables teams to capture application profiles in non-production clusters and apply them to production environments, enhancing security without compromising operational efficiency.
ARMO’s CDR workload protection component, based on Kubescape capabilities, consists of two main components:
1. Application Profile Builder: Uses eBPF to trace information and build detailed application profiles.
2. Detection Engine: Incorporates custom rules, anomaly detection, and behavioral inspection rules.
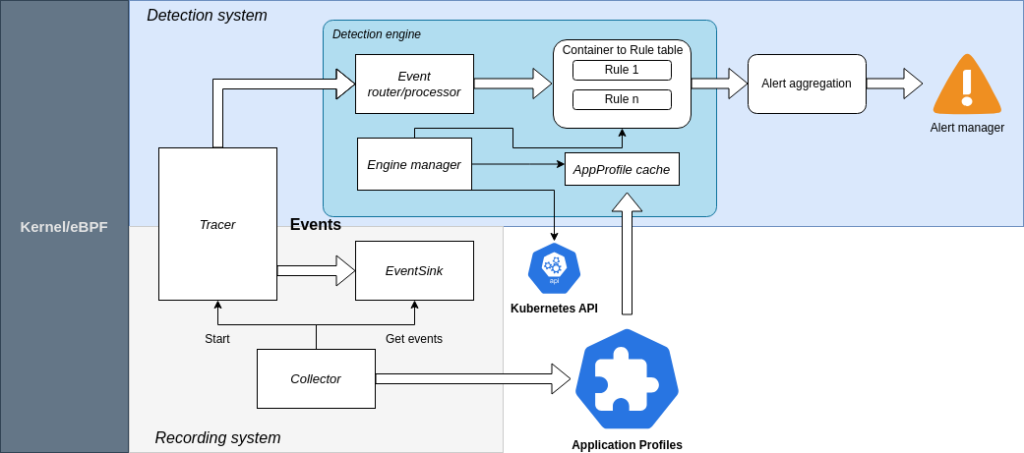
These components work together to provide a comprehensive runtime security solution that adapts to the specific needs of each Kubernetes environment and application running on it.
ARMO Platform combines otherwise unrelated signals into a security event to further alleviate alert fatigue. Consequently, all the information needed for security practitioners is gathered in one location, assisting with the root cause investigation and security event remediation.
As Cloud environments become increasingly complex, context-aware runtime anomaly detection offers a promising solution for enhancing security. By combining application profiling with anomaly detection and behavioral inspection, this approach provides a tailored method for identifying and mitigating security threats in containerized workloads.
The integration of such tools into existing DevOps workflows, through GitOps practices, showcases the potential for seamless adoption of advanced security measures in modern cloud-native architectures. As the field continues to evolve, we can expect further refinements and innovations in runtime security for Cloud environments.
Interested in enhancing your Cloud security? Try ARMO’s Behavioral-based Cloud Application Detection & Response.

We’re excited to announce that ARMO now fully supports Google Kubernetes Engine (GKE) Autopilot clusters!...

Software supply chain attacks cost businesses $45.8 billion globally in 2023 alone, and is projected...

Imagine this situation: you recently updated one of your infrastructure software components. A few weeks...