Kubescape Joins CNCF Incubation: A Major Milestone in Kubernetes Security
We’re excited to announce that Kubescape has officially entered the CNCF Incubating stage! This achievement...
![[NEW] Kubescape now integrates with GitHub Actions](https://www.armosec.io/wp-content/uploads/2022/12/Kubescape-Integrates-with-GitHub-Actions-1.png)
Dec 8, 2022
We are happy to announce that Kubescape now integrates with GitHub Actions. This allows users to identify issues as early and as clearly as possible, without ever leaving GitHub. Read all about it 👇
GitHub is where code happens for nearly 100M developers worldwide. More and more of these developers subscribe to the DevSecOps philosophy, which calls for developing applications securely from ideation to deployment. We know that in order for teams to fully embrace security, it needs to be accessible in existing tools. Ideally, it is embedded seamlessly into existing workflows.
GitHub Actions has made it easier than ever to build a secure continuous integration and continuous delivery (CI/CD) pipeline for your GitHub projects. By integrating your CI/CD pipeline and GitHub repository, GitHub Actions allows you to automate your build, test, and deployment pipeline. You can create workflows that build and test every pull request to your repository. You can also use it to deploy merged pull requests to production.
We are happy to announce that the ARMO Kubescape team has integrated Kubescape with GitHub code scanning. This allows you to identify issues as early and as clearly as possible, without ever leaving GitHub.
After Kubescape scans your code, you can navigate within the pull request (PR) and see all the alerts that Kubescape found for the changed file. These alerts are found in the exact place that Kubescape reported them. Within this context, you can drill deeper into the specifics. Kubescape provides information on the issue you select. This information includes a suggestion for a fix.
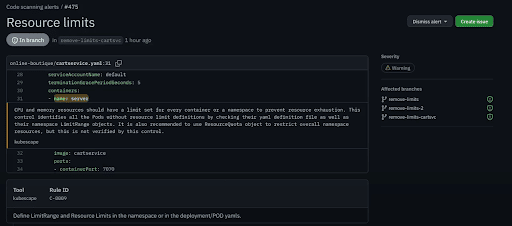
Information from Kubescape can also be accessed from the conversations tab on your PR. In the checks session, you will get additional Kubescape items. They are aggregated per type (i.e. misconfiguration scanning and code scanning results). Clicking on details will allow you to drill down into the detailed results of the specific topic.
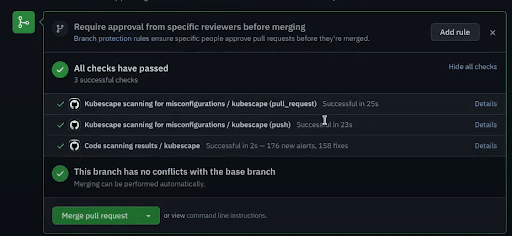
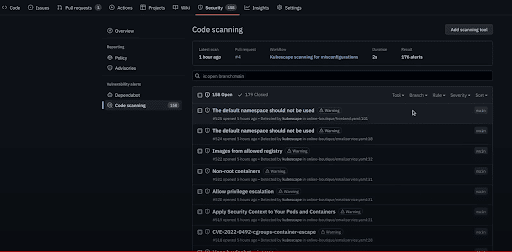
Lastly, you can also check out alerts for the current state of the branches you scanned in the past. You will find this under the GitHub security tab when selecting the code scanning option. You can now observe any new alerts Kubescape found. In this way, you can make sure that you are not experiencing configuration drift.
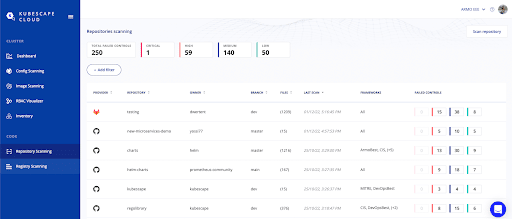
You can setup a GitHub secret with the Kubescape account ID, this way you will see the scanning results in the Kubescape Cloud in addition to the results in the GitHub security tab.
Setup:
name: Kubescape scanning for misconfigurations on: [push, pull_request] jobs: kubescape: runs-on: ubuntu-latest steps: - uses: actions/checkout@v3 - uses: kubescape/github-action@main continue-on-error: true with: format: sarif outputFile: results.sarif # Specify the Kubescape cloud account ID account: ${{secrets.KUBESCAPE_ACCOUNT}} - name: Upload Kubescape scan results to Github Code Scanning uses: github/codeql-action/upload-sarif@v2 with: sarif_file: results.sarif
Results:
Our goal at ARMO is to bridge the divide between security and engineering. This is possible by making the software development lifecycle security aware, without requiring every engineer to become a security expert. This integration makes it even easier for teams using GitHub to secure their infrastructure and improve DevSecOps efficiencies.
If you are not yet a Kubescape user, give us a try.

The only runtime-driven, open-source first, cloud security platform:
Continuously minimizes cloud attack surface
Secures your registries, clusters and images
Protects your on-prem and cloud workloads

We’re excited to announce that Kubescape has officially entered the CNCF Incubating stage! This achievement...

Guest post originally published on Kubescape’s blog by Oshrat Nir, Developer Advocate at ARMO and a Kubescape contributor. Introduction Admission control is a...

In this blog post we will be discussing how we differentiate ARMO Platform from Open...