Kubernetes 1.34 – Top Security Enhancements 💪
Kubernetes v1.34 is coming soon, and it brings a rich batch of security upgrades –...

Oct 24, 2023
ARMO addresses 76% of key concerns highlighted in the Red Hat 2023 Report.
We analyzed one of our favorite annual reports – the Red Hat State of Kubernetes security report 2023. It’s chock full of really interesting data on one of our favorite topics: Kubernetes security (Who knew?!)
In this post, we’ll unpack some of the most compelling data points and compare them to previous years. We’ll also share some of our own insights and perspectives on how this impacts you as a Kubernetes user.
If we had to summarize the report in the few short bullets that should matter to you, these are probably the primary takeaways from the data:
| 2023 | 2022 | 2021 | |
| Have you ever delayed or slowed down application deployment into production due to container or Kubernetes security concerns? | |||
| Yes | 67%⬆ | 55% | 55% |
| No | 33% | 45% | 45% |
| In the past 12 months, what security incidents or issues related to containers and/or Kubernetes have you experienced? | |||
| Misconfiguration | 45%⬇ | 53% | 59% |
| Security incident during runtime | 49%⬆ | 30% | 32% |
| Major vulnerability to remediate | 42%⬆ | 38% | 31% |
| Failed audit | 27%⬆ | 22% | 20% |
| What is your biggest concern about your company’s container strategy? | |||
| It isn’t taking security seriously or investing in security adequately | 38% | 31% | 45% |
| It is progressing too slowly | 25% | 22% | 15% |
| It doesn’t account for compliance needs | 14% | 6% | 14% |
| It doesn’t address skills gaps on our team | 13% | 20% | |
| It doesn’t account for cultural or process changes | 10% | 12% | |
| What role at your company is most responsible for container and Kubernetes security? | |||
| Ops (architect, platform, infrastructure, SRE, cloud) | 20% | 16% | 21% |
| DevOps | 18% | 43% | 27% |
| DevSecOps | 15% | 19% | 18% |
| Security (cloud security, security eng., InfoSec) | 28%⬆ | 16% | 18% |
| Developer | 20% | 6% | 15% |
| Do you have a DecSecOps initiative in your organization? | |||
| Yes – advanced stage | 45%⬆ | 27% | 25% |
| Yes – early stage | 39% | 50% | 49% |
| No | 17% | 22% | 26% |
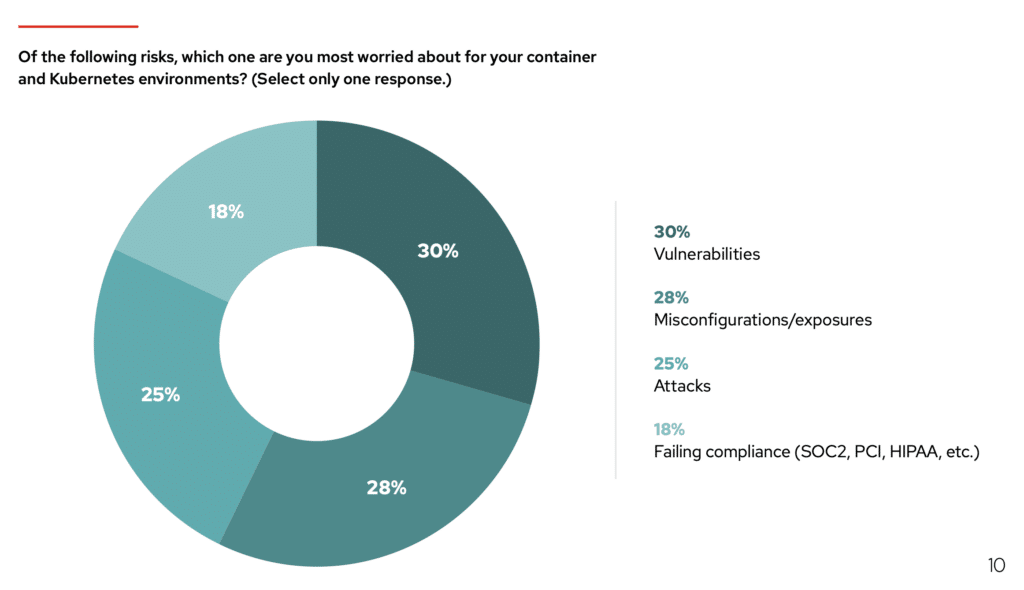
| Of the following risks, which one are you most worried about for your container and Kubernetes environments? | |||
| Vulnerabilities | 30% | 28% | 31% |
| Misconfigurations/exposures | 28%⬇ | 46% | 47% |
| Attacks | 25%⬆ | 16% | 13% |
| Failing compliance (SOC2, PCI, HIPAA, etc.) | 18%⬆ | 9% | 8% |
Let’s take a closer look at this last question from the table above.
ARMO invests a lot of effort to address the real security concerns of organizations deploying Kubernetes to production. This is highlighted by the fact that ARMO covers 76% of the concerns highlighted in the report.
This means that THREE of the top risks that concern developers and security practitioners today with regards to Kubernetes security can be managed with a single pane of glass, and a holistic view.
It’s interesting to note that while the majority of companies with security misconfiguration concerns have indicated that they are constantly taking steps to address them (page 11). Yet, this is still not easily solved. The source of friction concentrated on aspects of remediation. That is why ARMO has focused a lot of attention on deeply embedding remediation capabilities that run the gamut of integrations with common DevOps tooling. This, in addition to assisted remediation, and auto-remediation capabilities directly in GitHub through fix PRs with a practical solution.
The extensive vulnerability and misconfiguration coverage is made possible through the number of controls available out of the box, with more than 200+ controls (the most available on the market today), that are based on the industry standards noted above. This is also the backbone for ARMO Platform’s continuous compliance capabilities, that are rooted in all of the above.
Security practitioners can monitor Kubernetes clusters with confidence using dashboards that indicate drift, provide immediate notifications of misconfigurations and new vulnerabilities. This comprehensive solution includes contextual security data, offering both informative and actionable insights. Best of all, it eliminates the need for extensive manual efforts or building from scratch.
The Red Hat State of Kubernetes Security report 2023 highlights the evolving landscape of Kubernetes security. While concerns have shifted towards actual attacks and compliance failures, concerns related to misconfigurations have decreased. Vulnerability counts remain a consistent concern, and runtime incidents and vulnerabilities are rising, leading to more delayed deployments.
ARMO Platform is a comprehensive solution that covers 76% of the concerns raised in the report. It offers automated vulnerability assessment and remediation of misconfigurations. It provides dashboards, immediate notifications, and contextual security data for holistic monitoring of Kubernetes clusters. With this Kubernetes security tool, organizations can confidently navigate Kubernetes security, ensuring hardened and compliant infrastructure.

The only runtime-driven, open-source first, cloud security platform:
Continuously minimizes cloud attack surface
Secures your registries, clusters and images
Protects your on-prem and cloud workloads
Kubernetes v1.34 is coming soon, and it brings a rich batch of security upgrades –...
At ARMO, our mission is to make Kubernetes security more accessible, actionable, and effective. That’s...

We’re excited to announce that ARMO now fully supports Google Kubernetes Engine (GKE) Autopilot clusters!...