Eliminate Kubernetes Misconfigurations <br/> from your <br/> {<mark>CI/CD pipeline</mark>}
<p><span style="font-weight: 400;">Over 100 K8s-specific controls and dedicated frameworks to scan, detect and fix misconfigurations from the moment you write your first YAML line, up to production.</span></p>
+80K
Downloads
+50K
Users
Kubernetes security single-pane-of glass
- Kubernetes security risk analysis & compliance
- End-to-end Kubernetes scanner - Registries & Images scanning, git code repositories, manifest files, worker nodes and API servers
- RBAC visualization and investigation
Readymade DevSecOps platform
- Built-in UI, 3-6 months data retention
- Easily integrated with leading DevOps tools
- Instant K8s risk scoring, see historical scans, identify configuration drifts, set exceptions, risk trends over time;
Value in less <br/>than 3 min
- Detect & Fix misconfigurations, vulnerabilities and RBAC violations FAST
- Instant view of failed K8s resources with fix recommendations
- Quick remediation, contextual insights
Kubernetes configuration scanning()
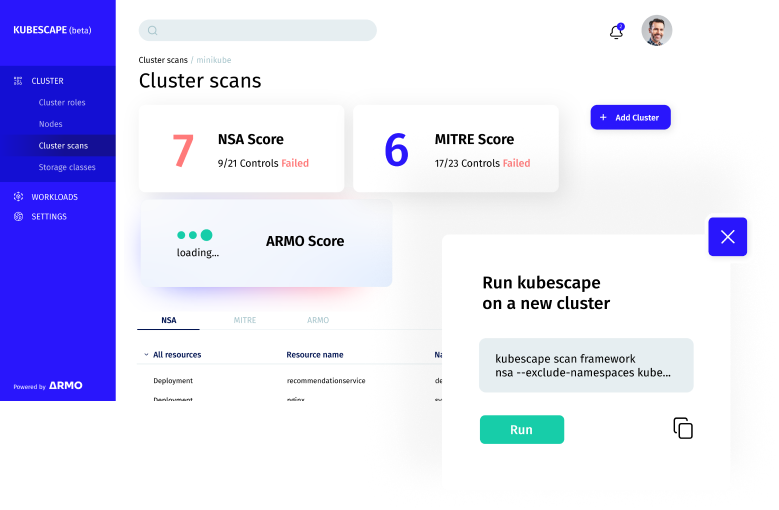
<ul>
<li style="font-weight: 400;" aria-level="2"><span style="font-weight: 400;">Scan code repositories, manifest files (YAML, Helm), K8s clusters, worker nodes, and API servers;</span></li>
<li style="font-weight: 400;" aria-level="2"><span style="font-weight: 400;">Define and enforce Kubernetes security best practices against multiple frameworks as NSA-CISA, CIS, MITRE, K8s Best Practices, or create your own custom one</span></li>
<li style="font-weight: 400;" aria-level="2"><span style="font-weight: 400;">Identify and prevent configurations drifts continuously, from CI/CD to Production</span></li>
<li style="font-weight: 400;" aria-level="2"><span style="font-weight: 400;">Get instant K8s risk score, see history of past scans and learn risk trends overtime;</span></li>
</ul>

Kubernetes & containers vulnerabilities scanning()
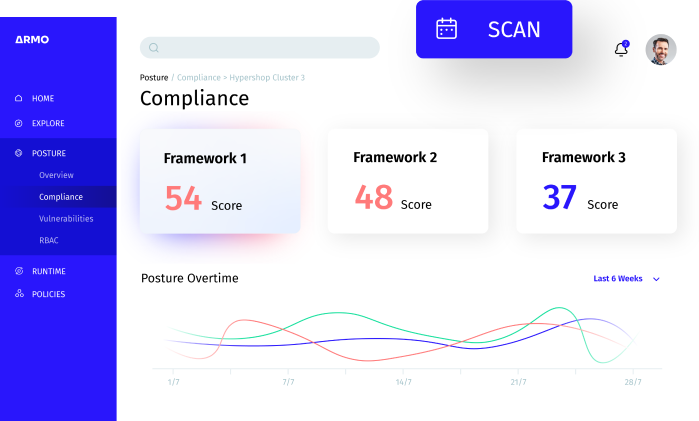
<ul>
<li style="font-weight: 400;" aria-level="2"><span style="font-weight: 400;">Continuously scan images registries and containers’ images for vulnerabilities;</span></li>
<li style="font-weight: 400;" aria-level="2"><span style="font-weight: 400;">Easily identify, prioritize, and filter which vulnerability to patch first;</span></li>
<li style="font-weight: 400;" aria-level="2"><span style="font-weight: 400;">Continuous Kubernetes security tightening and attack surface reduction</span></li>
</ul>

Kubernetes RBAC made easy()
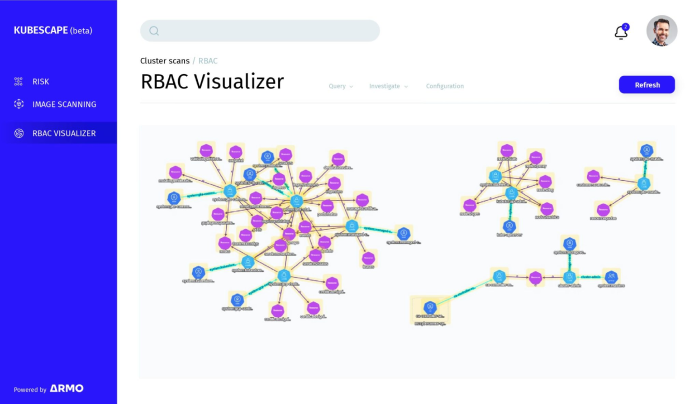
<ul>
<li style="font-weight: 400;" aria-level="2"><span style="font-weight: 400;">Visual RBAC configuration graph with Easy-to-use and easy-to-understand;</span></li>
<li style="font-weight: 400;" aria-level="2"><span style="font-weight: 400;">RBAC configuration built-in queries – What you need to be aware of;</span></li>
<li style="font-weight: 400;" aria-level="2"><span style="font-weight: 400;">Customized RBAC investigation tool;</span></li>
</ul>

Run within your CI/CD()
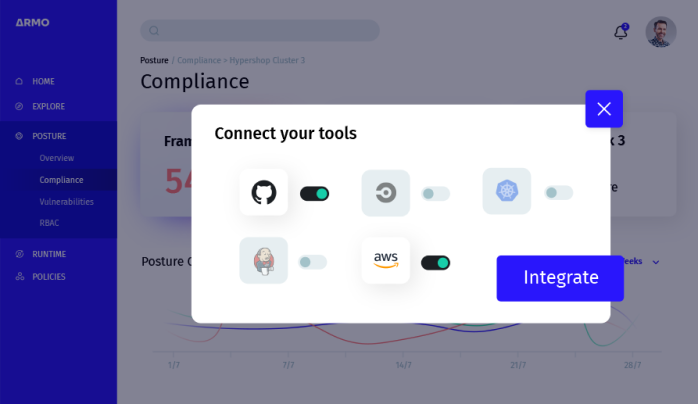
<ul>
<li style="font-weight: 400;" aria-level="1"><span style="font-weight: 400;">DevOps first experience </span></li>
<li style="font-weight: 400;" aria-level="1"><span style="font-weight: 400;">Embed security into any stage of your SDLC – from configuration to production</span></li>
<li style="font-weight: 400;" aria-level="1"><span style="font-weight: 400;">Simple integration to your favorite pipeline tools including Jenkins, CircleCI, Gitlab, Github workflows, Prometheus, Lens, Slack, and more;</span></li>
<li style="font-weight: 400;" aria-level="1"><span style="font-weight: 400;">Supports multi-cloud K8s deployments like EKS, GKE, and AKS</span></li>
<li style="font-weight: 400;" aria-level="1"><span style="font-weight: 400;">Easy to use CLI interface and flexible output formats;</span></li>
<li style="font-weight: 400;" aria-level="1"><span style="font-weight: 400;">API Based with read-only Privileges;</span></li>
</ul>

Trusted by
50,000
[Users]
From
914
[companies]









