Kubernetes_RBAC
made easy
Loved by DevOps and trusted by Security at_
Your RBAC, visualized.
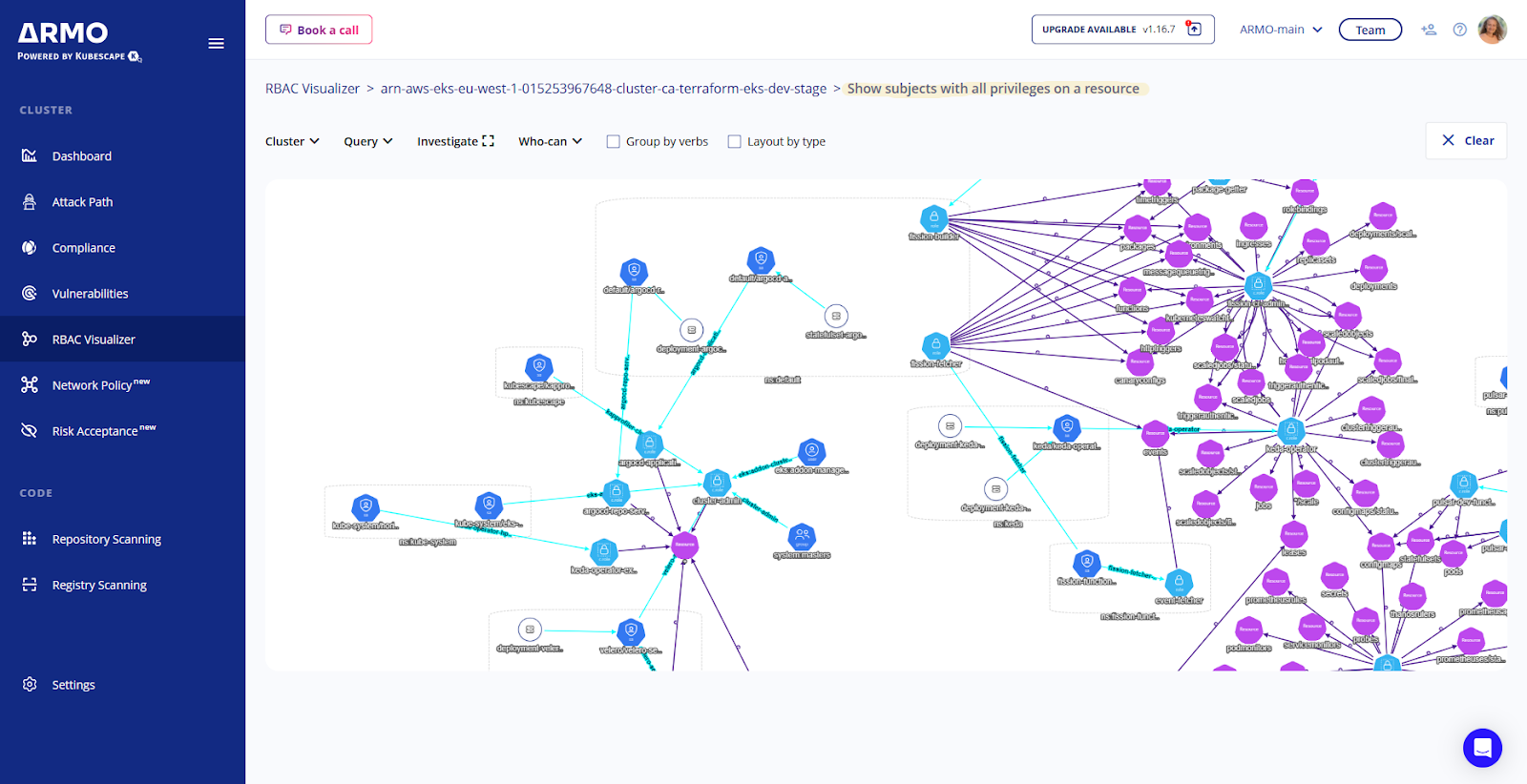
Easily view and investigate the permissions in your system with a comprehensive and dynamic visual RBAC configuration graph. Use built-in queries to reveal the permissions that result from your RBAC configuration. Easily generate custom queries to analyze the permissions that matter most to you.
Kubernetes RBAC made easy
Graph all roles, resources, and role-bindings. Run pre-defined queries and reveal RBAC insights. Find who has access to Kubernetes components using NLP-like queries. Perform deep RBAC analysis up to a single role and resource.
Full visibility, full control
ARMO platform includes an RBAC visualizer allowing administrators to see which privileges are assigned to any given user. With ARMO Platform, administrators can take control of RBAC management and reduce the attack surface by conforming to the principle of least privilege.
A smart K8s RBAC investigator
Are you really in control of the access to your Kubernetes resources? Find anonymous users and subjects with privileges on all resources, in one click. Use built-in queries to reveal the most important RBAC insights and enjoy customized RBAC investigation tool.
The value our users see in ARMO Platform



{Flexible hosting options}
Hosted by ARMO
We’ll host your ARMO Platform instance and retain your data (SOC 2 compliant), according to the plan you are on.
In your cloud
Install ARMO Platform as a private tenant on your cloud provider account and host your data yourself.
On-Prem
Install ARMO Platform on your on-prem machines





