GitOps — Enhancing security and ensuring compliance in Kubernetes deployments
GitOps can be a powerful means of achieving continuous compliance in Kubernetes deployments. It provides...
GitOps can be a powerful means of achieving continuous compliance in Kubernetes deployments. It provides...

While Kubernetes adoption continues to soar, it has become a prime target for cyberattacks. Unfortunately,...
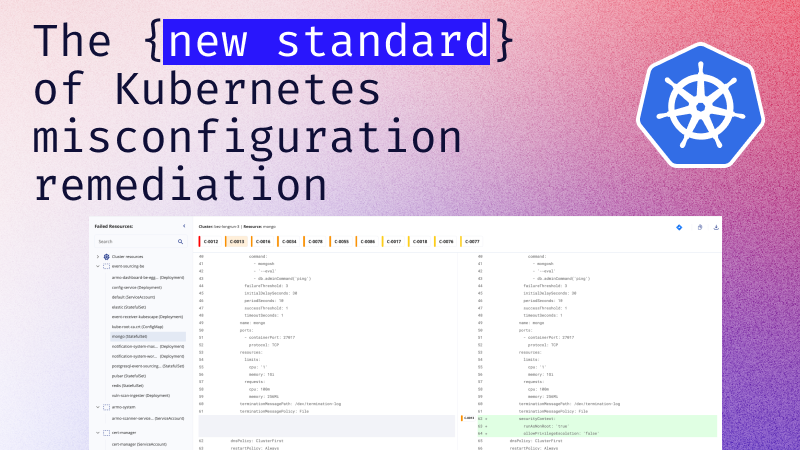
According to research done by ARMO, 100% of Kubernetes clusters that were tested contained at...
In this post we’re going to unpack some of Red Hat State of Kubernetes security...
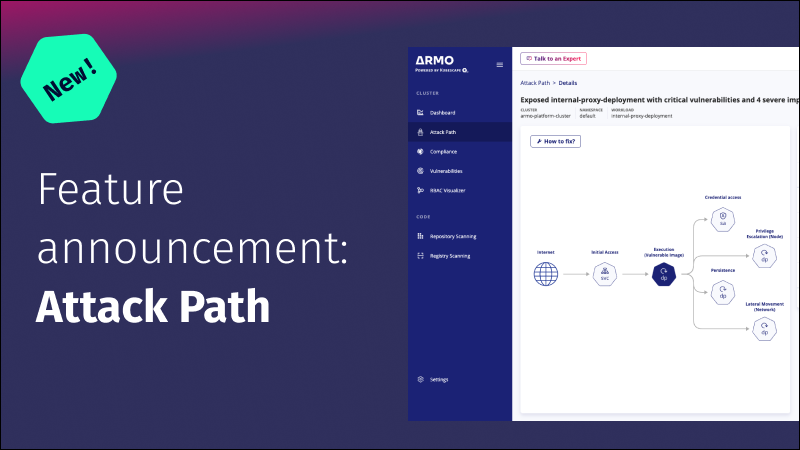
Discover the importance of mapping attack paths in Kubernetes and learn how to effectively enhance...
Kubernetes misconfigurations can create security risks and other issues. This article covers common types, their...

Kubernetes has become the de facto platform for orchestrating containerized applications at scale in today’s...
Guest post originally published on DevOps Journey by Brad Morgan. How do I keep...
RBAC management is crucial to securing a Kubernetes cluster and ensuring compliance with regulations and...
Security gaps in a Managed Kubernetes Environment - In this article, we examine the impact...

This post compares popular Kubernetes security and compliance frameworks, how they differ, when to use...

Discover the complex bond between AI and software development, as malicious actors exploit AI code...