ARMO named in Gartner® Cool Vendors™ report
We are excited and honored to announce that we were selected as Gartner Cool Vendor...

Aug 22, 2023
Kubernetes has become the de facto platform for orchestrating containerized applications at scale in today’s IT landscape. Its ability to run on various platforms including on-premises, public cloud, and hybrid has made it an essential tool for many organizations. This is particularly true for companies following a multi-cloud strategy, relying on more than one vendor for their cloud computing needs. Such an approach offers numerous benefits, like avoiding vendor lock-in, improved reliability, and optimized costs.
Properly securing Kubernetes in a multi-cloud environment is vital for businesses, given the sensitive data these apps often handle. However, the heterogeneous nature of multi-cloud deployments can also complicate security efforts. Each cloud provider has unique security controls and configurations, leading to potential inconsistencies in policy enforcement across different clouds.
These complexities underline the importance of making sure you implement security policies and practices consistently across all your cloud environments, a topic we will explore in this post.
It’s critical to first understand that Kubernetes presents some unique concerns. Kubernetes is designed to enable connectivity between applications and services by default. While this facilitates communication and integration, it also increases the potential attack surface that malicious actors can exploit.
In addition, Kubernetes deployments are dynamic and complex, with containers frequently being created, updated, and destroyed. This constant flux can make maintaining a clear view of your current security state challenging, especially when deployments are spread across multiple clouds. This heterogeneity can also make it tough to establish and maintain a unified security posture across all the different environments.
Given its complex nature, a one-size-fits-all approach to security won’t work in a multi-cloud environment. Instead, organizations need a unified security strategy that considers the specific security concerns of Kubernetes and the intricacies of a multi-cloud setup. You need to enforce consistent security controls across all environments, ensuring that no part of any deployment is left vulnerable.

When securing Kubernetes in a multi-cloud environment, you will have to handle several challenges, which we discuss below.
Each cloud provider offers distinct security features. For example, Azure offers AKS with a Hardened access tier, which provides the full set of security tools Azure has to offer, but at an additional price. This reflects the premium nature of the elevated security levels offered. On the other hand, AWS CloudTrail is geared towards governance, compliance, and ops/risk audits for AWS users; it also has an additional cost when the collected data is analyzed and CloudTrail Insights are provided.
It’s important to note that the operational security tasks can vary significantly depending on the provider. This variability can lead to potential lock-in scenarios.
Organizations must protect any data stored and processed in Kubernetes clusters. The encryption of stored secrets, proper access control, and ensuring the correct configuration for any new workloads are all critical aspects here.
IAM is a fundamental security component of multi-cloud. However, it can become complex in the context of Kubernetes due to different cloud environments and access control systems. In addition, Kubernetes itself brings its own access control mechanisms that most cloud providers fail to control adequately.
The network configurations for Kubernetes can greatly differ across cloud environments, requiring a nuanced understanding of each system to ensure proper security configurations. These network settings aren’t necessarily locked down by default. Users must secure their cloud resources themselves under the shared responsibility model. This means they need to be intentional and proactive about implementing and managing their security measures, including locking down their network configurations, to effectively protect their cloud environments.
Visibility into your Kubernetes deployments across all cloud environments is critical for effective monitoring and quick incident response. However, each cloud provider has its own set of monitoring tools and services, which may or may not integrate well with each other. This makes it challenging to maintain a unified view of your system’s state.
Another issue arises with compliance in multi-cloud since the different providers may have separate compliance controls and reporting mechanisms. This means that enforcing compliance across environments can require considerable effort. Cloud providers may use different compliance rules, which might not match those selected by your organization. Also, the number of controls supporting these rules varies between providers. All of this can lead to unnoticed gaps in compliance, making it vital to understand and account for these variations to maintain strong compliance in multi-cloud settings.
Such challenges indicate the need for a well-defined strategy when deploying Kubernetes in a multi-cloud ecosystem. Organizations should clearly define their multi-cloud orchestration use case. They should understand the various deployment options, and select the most suitable deployment model based on their specific goals and security needs.
In the next section, we will explore the best practices to mitigate these concerns and enhance the security of Kubernetes deployments in multi-cloud.
Given the complexities discussed when securing Kubernetes in multi-cloud environments, adopting some best practices will significantly enhance your security posture.
Kubernetes provides several security features out of the box, such as the ability to run containers with a non-root user and limit container permissions. However, you may need to configure these features manually since they are often not enabled by default.
Network policies and segmentation are essential to Kubernetes security. By controlling traffic between your pods, network policies restrict the potential attack surface and prevent lateral movement within your cluster. In addition, consider segmenting your Kubernetes deployments based on factors like environment (dev, test, prod), application, or data sensitivity.
Regularly audit your Kubernetes clusters to identify and fix misconfigurations or vulnerabilities. It would help if you also implemented comprehensive monitoring to keep track of your system’s state and quickly identify any abnormal behaviour. A centralized logging solution will enable you to gather and view logs from your cloud environments for a unified view.
Kubernetes provides features such as resource quotas and limit ranges to control the resources (CPU, memory, storage, etc.) that a namespace or pod can use. Enforcing these can help prevent resource exhaustion attacks and ensure that no single application or user can monopolize your cluster’s resources.
Namespaces in Kubernetes allow you to isolate your workloads from each other. This can be particularly useful for separating sensitive workloads or segregating different environments. Implementing proper Kubernetes RBAC policies at the namespace level can further enhance security.
Now, let’s look at some tools and techniques you can use to implement these best practices and boost the security of your Kubernetes deployments in multi-cloud environments.
Ensuring robust security in a multi-cloud environment is not straightforward; however, several options address different facets of this complex ecosystem.
A crucial feature of Kubernetes security, RBAC granularly manages who can access specific resources within the Kubernetes API and how those users can interact with them based on their roles. Implementing RBAC helps enforce the principle of least privilege, mitigating the risk of unauthorized access or actions. However, it gets complex as the number of roles grows, leading to a phenomenon known as role explosion.
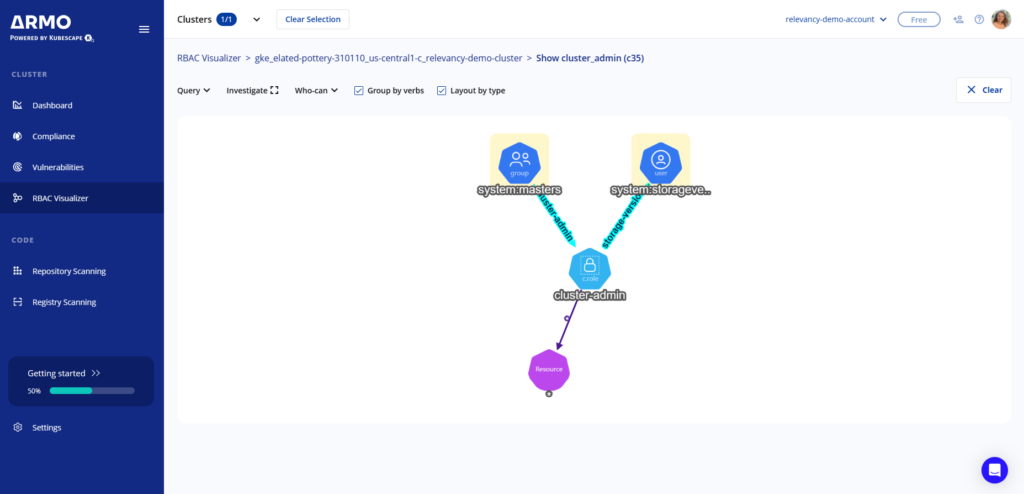
Visualization tools such as the one in ARMO Platform can help manage this complexity. ARMO provides an intuitive and graphical representation of the relationships between roles and bindings, helping administrators:
Kubernetes features a built-in admission controller known as Pod Security admission. This controller plays a pivotal role in defining and enforcing security conditions a pod must meet to run in the cluster. This includes parameters such as running containers in non-privileged mode and other measures to provide an essential layer of security to your Kubernetes clusters.
Secrets management is integral to securing sensitive data like tokens, passwords, and certificates. Tools like HashiCorp Vault and AWS Secrets Manager offer encryption, secure storage, and fine-grained control over access to this data. By using these tools, you can significantly lower the risk of a breach and prevent critical data from being exposed.
Leveraging native security solutions from your cloud provider can add an extra layer of protection and visibility for your Kubernetes deployments. Tools like AWS Security Hub, Microsoft Defender for Cloud, and Google’s Security Command Center boast features such as threat detection, incident response, compliance reporting, and security analytics.
These solutions are fundamental to enhancing the security of Kubernetes in multi-cloud environments. However, most of them cover only a small piece of security, while organizations need a more comprehensive approach.
There are additional tools you can leverage that provide a suite of capabilities to enhance the security of your Kubernetes deployments.
Aqua offers comprehensive security capabilities for containerized applications. It includes vulnerability scanning to detect and remediate vulnerabilities in container images, runtime protection to monitor and prevent unauthorized access or malicious activities within containers, and compliance and policy enforcement to ensure adherence to security standards.
Prisma Cloud Compute, is a container security tool that focuses on vulnerability management, compliance, and runtime protection. It scans container images for vulnerabilities and makes sure they adhere to your internal security policies as well as any regulatory requirements.
Armo Platform, powered by Kubescape, is a Kubernetes security platform with unique features we will discuss in the following section.
ARMO Platform is an advanced Kubernetes security platform that addresses the specific security challenges of multi-cloud environments. ARMO takes a holistic approach, focusing on critical areas such as misconfiguration and vulnerability management, compliance, and RBAC. ARMO Platform helps identify potential security risks in Kubernetes deployments and provides recommendations for remediation. With its support for end-to-end Kubernetes security, organizations gain a centralized view of and control over their Kubernetes security posture.
ARMO Platform offers several features to optimize Kubernetes security in multi-cloud:
As organizations embrace multi-cloud architectures, it is crucial to account for the complexities it introduces to Kubernetes security. The challenges of securing Kubernetes in multi-cloud and on-premises environments necessitate a robust and comprehensive security solution.
ARMO Platform offers misconfiguration and vulnerability management, compliance and governance, and RBAC visualization—everything organizations need to secure their Kubernetes deployments effectively on any public or private cloud. Give ARMO a try today. Protect your Kubernetes workloads with confidence and ensure a strong security posture across your clouds.

The only runtime-driven, open-source first, cloud security platform:
Continuously minimizes cloud attack surface
Secures your registries, clusters and images
Protects your on-prem and cloud workloads

We are excited and honored to announce that we were selected as Gartner Cool Vendor...

We’re excited to announce that ARMO now fully supports Google Kubernetes Engine (GKE) Autopilot clusters!...

Software supply chain attacks cost businesses $45.8 billion globally in 2023 alone, and is projected...