How to Compare Cloud Security Tools: The Evaluation Framework
Key Insights Introduction You’re not struggling to find cloud security tools. You’re struggling to compare...
May 29, 2025
Let’s be honest. Most cloud security alerts feel like trying to read a book with half the pages missing. You get bits and pieces — “unusual login,” “suspicious process,” “network traffic spike” — but no real explanation of what actually happened or what you should do about it.
That’s the daily reality for security teams. You’re not just fighting attackers; you’re fighting for context.
Your alert system fired, again. But this one’s different. It started as just another login anomaly. But what if it wasn’t? What if that alert was the first sentence of a much bigger story, one involving stolen credentials, lateral movement, and an attacker creating their own backdoor into your cloud?
That’s exactly what happened in a recent incident. And how you read the story makes all the difference.
Too often, cloud security incidents are delivered in pieces: a failed login here, a system call there, a new S3 bucket in another dashboard. None of it makes sense until someone — usually a burned-out security analyst — manually pieces it together.
The result?
🔸 Real threats go undetected for too long
🔸 Teams waste time chasing false positives
🔸 SOC teams must engage other departments — cloud, DevOps, platform, developers — just to get access to the right logs
Why is it like this?
Because today’s runtime security tools are siloed by design.
🔹 ADR (Application Detection and Response) watches app-layer activity
🔹 CDR (Cloud Detection and Response) monitors cloud-native events
🔹 EDR (Endpoint Detection and Response) looks at host behavior
Each one sees only a fragment of the stack – and none tells the full story.
So by the time the full picture comes into focus, it’s too late.
Every incident is made up of events. But when those events come in as disconnected alerts, it’s on the security analyst to stitch them together. And that takes time — time you often don’t have during an active threat.
You might spend hours digging through logs or jumping between tools just to answer three basic questions:
🟡 What exactly happened?
🟡 Is it a real threat?
🟡 What should we do next?
This is where storytelling comes in.
Not the bedtime kind — the kind that makes technical incidents make sense fast.
What if you didn’t have to reconstruct the story?
Imagine if your system could say:
“A SQL injection was used to extract user data. Minutes later, AWS credentials were harvested, and a rogue IAM user was created to set up exfiltration buckets.”
That’s not an alert. That’s a story you can act on → fast.
This is what we mean by narrative-driven incident intelligence: clear, contextual, human-readable explanations of what just happened, why it matters, and what to do next.
At ARMO, we’ve built incident storytelling into the heart of our platform. Here’s how we do it:
✅ Code-to-Cloud Contextual Detection – A fully explainable and traceable runtime security story that spans the entire cloud technology stack. ARMO connects low-level system signals, API calls, code execution, and network behavior to reconstruct the complete chain of events, enabling precise, context-rich threat detection and response.
✅ Auto-Generated Narratives – Our platform uses real-time data to build an incident story – not just what happened, but why and what’s next.
✅ Response Recommendations – Alongside each narrative, we offer clear remediation steps so teams can act fast with confidence.
Imagine getting a cloud incident alert that doesn’t just say “unauthorized access attempt” but instead tells you:
And most importantly — you didn’t have to piece it all together yourself.
That’s not just helpful. That’s game-changing.
Before:
9:35 AM – Unknown SQL input detected.
9:37 AM – System call getxattr observed.
9:38 AM – New S3 bucket created.
…You’re left guessing.
After (with ARMO):
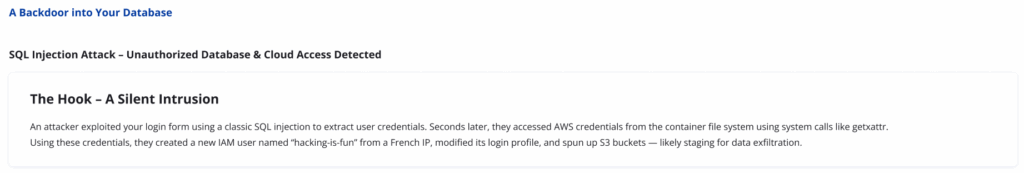
An attacker exploited your login form using a classic SQL injection to extract user credentials. Seconds later, they accessed AWS credentials from the container file system using system calls like getxattr. Using these credentials, they created a new IAM user named “hacking-is-fun” from a French IP, modified its login profile, and spun up S3 buckets — likely staging for data exfiltration.
Now you’re not guessing — you’re responding.
When cloud incidents are presented as stories, everything gets easier:
🔹 Reduce investigation time by 90% – You understand the situation in seconds, not hours
🔹 Triage real threats instantly – Context helps you focus on real threats with fewer false positives
🔹 Better and faster collaboration – You can actually share the incident with non-security folks and they’ll get it.
🔹 Strengthen your cloud posture with actionable insights, not alerts
🔹 Stronger response – With a clear picture, you can act decisively
⇒ That’s not a small win — that’s the difference between catching an attacker in real time and finding out after the damage is done.
This wasn’t hypothetical.
A production login service was hit with an SQL injection at 9:35 AM.
Two minutes later, system-level calls indicated reconnaissance activity.
By 9:38 AM, a new IAM user was created in AWS, along with two suspicious S3 buckets.
The attacker had moved from application to cloud — and was building infrastructure inside someone else’s account.
ARMO’s real-time incident story connected the dots.
The team acted within minutes — killing the rogue IAM user, rotating credentials, and blocking the attacker’s IP before exfiltration occurred.
Cloud complexity is exploding. Applications, Kubernetes, serverless, containers – it’s all dynamic and distributed. If anything, they’re growing more dynamic, interconnected, and fast-moving.
Attackers love this chaos. And legacy alert systems only make it worse.The tools that throw out raw signals without explanation just aren’t enough anymore.
Security teams need something that keeps up – not just technically, but cognitively. Something that doesn’t just alert, but explains.
That’s what narrative-driven security is all about. And it’s already here.
If you’re still wading through logs and bouncing between alerts just to understand what’s going on, maybe it’s time to let the incident tell its own story. One that’s clear, actionable, and for once actually helpful.
Want to know what your next cloud incident is really telling you?
👉 Watch a demo and see how ARMO turns raw signals into clear, actionable stories — in real time.

Key Insights Introduction You’re not struggling to find cloud security tools. You’re struggling to compare...

Key Insights What is the best eBPF security tool for Kubernetes? For detection-only, Falco. For...

Key Insights What are the three types of cloud compliance tools? Audit-prep platforms (Drata, Vanta)...