IngressNightmare: Analysis of Critical Vulnerabilities in Kubernetes Ingress NGINX Controller
Executive Summary On March 24, 2025, Wiz Research disclosed a series of critical vulnerabilities in...

Dec 21, 2022
Security researchers at ARMO have found a high-severity vulnerability in the Kyverno admission controller container image signature verification mechanism. The vulnerability enables an attacker who is either running a malicious container image registry or is able to act as a proxy between the registry and Kyverno, to inject unsigned images into the protected cluster, bypassing the image verification policy.
The vulnerability was introduced in version 1.8.3 and was fixed in version 1.8.5. We recommend all Kyverno users update as soon as possible.
Supply chain security is a thoroughly discussed topic in the Cloud Native community. It comes as no surprise that projects like Kyverno have started to incorporate supply-chain security measures into their offerings.
In order to secure supply chains, validation of software components should happen at every step from development to production. Container images are an obvious potential attack vector, so it is critical that they are validated to ensure that only verified code is running in a Kubernetes cluster. If an attacker is able to control the contents of an image that is pulled into the cluster, the attacker can effectively take control of a victim’s pod and use all of its assets and credentials, including the service account token to access the API server.
In order to protect a Kubernetes cluster against malicious container images, security-focused admission controllers offer policies that can enforce container image signatures. Their promise is that with an admission controller, users can create a policy to only have validated images running inside the cluster.
Here is the way signature validation works in the Kyverno admission controller.
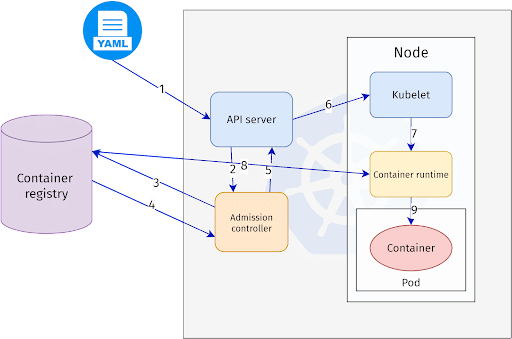
An attacker’s goal may be to inject an unsigned image into a cluster which should only be running signed images.
In this attack, we assume the attacker controls a malicious container registry or has set up a proxy between the registry and the target. The attacker attempts to trick the user into running a Pod with an image from this registry. Meanwhile, the cluster administrator has a policy in place to protect the cluster from malicious images by enforcing container signatures. From the cluster administrator’s perspective, no unsigned images can be admitted into the cluster.
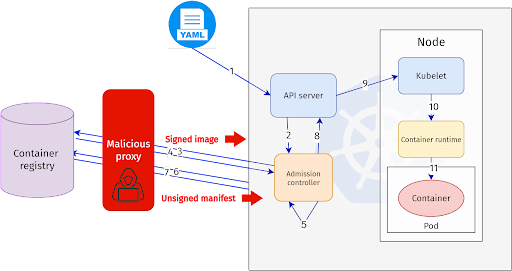
The attack steps are as follows:
The problem is that the image manifest is downloaded twice. It is pulled once for signature validation and a second time for mutating the image name in the Pod spec. This is a classic example of a TOCTOU problem that allows the attacker to pull a bait-and-switch. Since the image manifest which will eventually be used is not the same as the one which was verified, this enables the attacker to trick the client.
Kyverno implements a mechanism to verify container images against supply chain attacks. It automatically substitutes the image tag for the digest on first use. However, a bug introduced in Kyverno 1.8.3 can cause multiple tag-based queries to the image registry, which can be exploited by attackers. This problem has been fixed promptly by the Kyverno team, in version 1.8.5, and users should update to the latest version. The fix ensures that the same image hash is used to change the workload specification as was used to verify the signature.
Additional recommendations:
curl -s https://raw.githubusercontent.com/armosec/kubescape/master/install.sh | /bin/bash kubescape scan control C-0091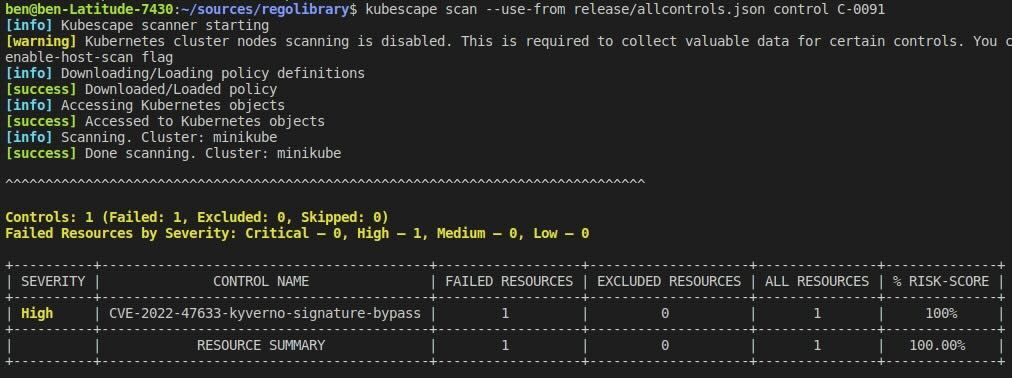
Executive Summary On March 24, 2025, Wiz Research disclosed a series of critical vulnerabilities in...

Imagine this situation: you recently updated one of your infrastructure software components. A few weeks...
In 2024, several significant vulnerabilities were identified within the Kubernetes and broader cloud-native ecosystem. In...