Three New High-Severity Vulnerabilities in runc: What You Need to Know
Within 24 hours, three new high-severity vulnerabilities were disclosed in runc, the low-level runtime that...

Feb 20, 2024
Struggling to manage vulnerabilities in your Kubernetes environment? You’re not alone. Traditional vulnerability management tools often leave security teams feeling overwhelmed and unsure of where to focus their efforts. Traditional scanners churn out an endless stream of alerts, many irrelevant, making it difficult to prioritize and address the most critical issues. Sound familiar?
As a security professional, to reach the goal of achieving and maintaining a strong Kubernetes security posture, you need to streamline resource allocation for maximum impact on security. To achieve this you must efficiently prioritize vulnerabilities based on their potential exploitability.
This could mean a lot of manual work and hours of research, or you can use ARMO Platform’s new risk-based approach to vulnerability management in Kubernetes.
ARMO Platform helps streamline vulnerability management, ensuring your systems remain secure and resilient. Here’s a look at some of the key improvements:
ARMO Platform enables precise vulnerability prioritization by considering workload context, exploitability, severity, runtime analysis, and fixability. This comprehensive approach ensures that you address the most critical vulnerabilities first, minimizing potential risks to your infrastructure.
Stay ahead of emerging threats with real-time insights gathered from multiple threat intelligence sources, including CISA KEV and EPSS, as well as the Common Vulnerability Scoring System (CVSS). By combining this data with specific vulnerable components, you can quickly spot actively exploitable vulnerabilities and take proactive steps to address them.
ARMO Platform empowers you to assess your risk posture effectively by answering crucial questions such as:
With these advanced capabilities, you can make informed decisions and strengthen your organization’s security posture, safeguarding your assets against potential threats.
ARMO Platform automatically analyzes and scans the container image of your workloads. It gives you a list of vulnerable workloads, and a Risk Spotlight, so you can concentrate on addressing the current, critical, and exploitable vulnerabilities.
The workloads page lists the workloads scanned by ARMO Platform ordered by the most vulnerable.
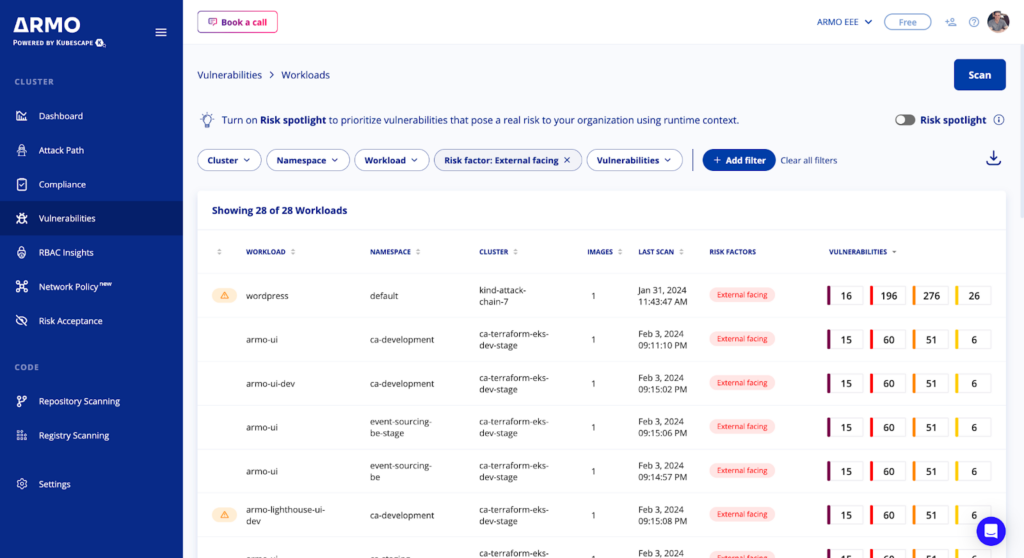
It allows users to filter results according to risk factors such as:
Additionally, turning data into information, the Smart vulnerabilities filter helps users focus on workloads that have vulnerabilities that fall under the following criteria:
Risk spotlight prioritizes vulnerabilities that pose a real risk to your organization using workload configuration, runtime context, exploitability, severity, and fixability. Thus, reducing the noise of your CVE scanning results by >90% and helping you focus on the alerts that actually matter.
For any organization, there could be a large number of vulnerabilities, considering the number of workloads and images. To make fixing them more manageable, Risk Spotlight adds a new way of prioritizing vulnerabilities based on runtime behavior. It significantly reduces the number of vulnerabilities that you initially think need immediate attention, making the vulnerability management process more effective.
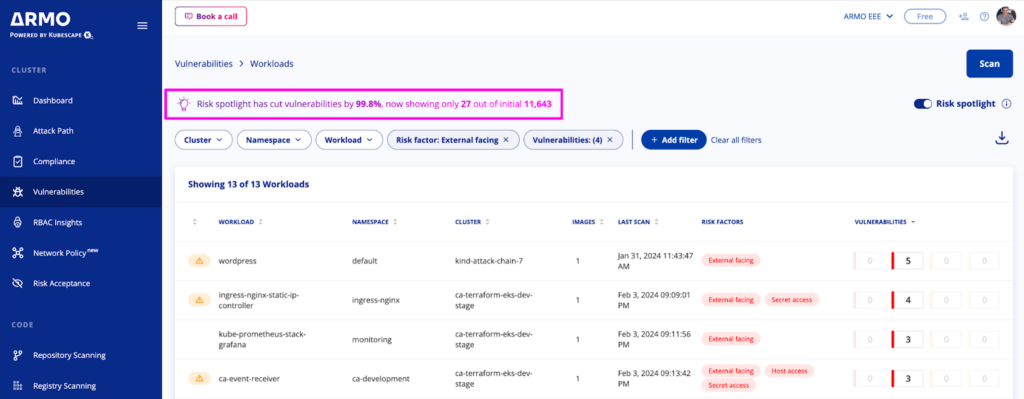
It does this by combining the following information:
This approach guides users to prioritize workloads at the highest risk and minimizes the noise generated by traditional CVE scanners, reducing it by over 90%. As a result, it helps you concentrate on alerts that are truly significant.
This screen provides an overview of all the workload details such as cluster, namespace, risk factors, labels, and vulnerabilities by severity.
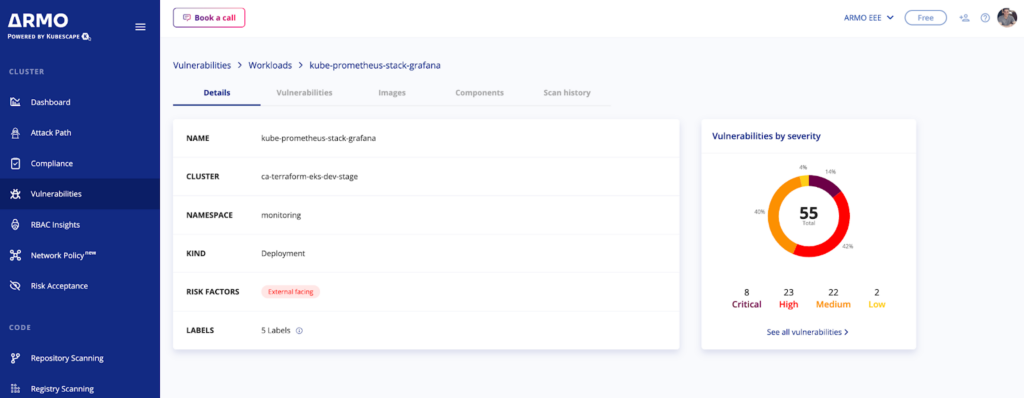
To get more information, you can activate the risk spotlight toggle and select a vulnerability tile on the results screen that is associated with a specific vulnerability. This will provide a deeper understanding of the potential risks to their workload and offer guidance on how to mitigate them.
By accessing the Vulnerability details page, users can explore various risk spotlight filters and access recommendations for resolving any exploitable vulnerabilities.
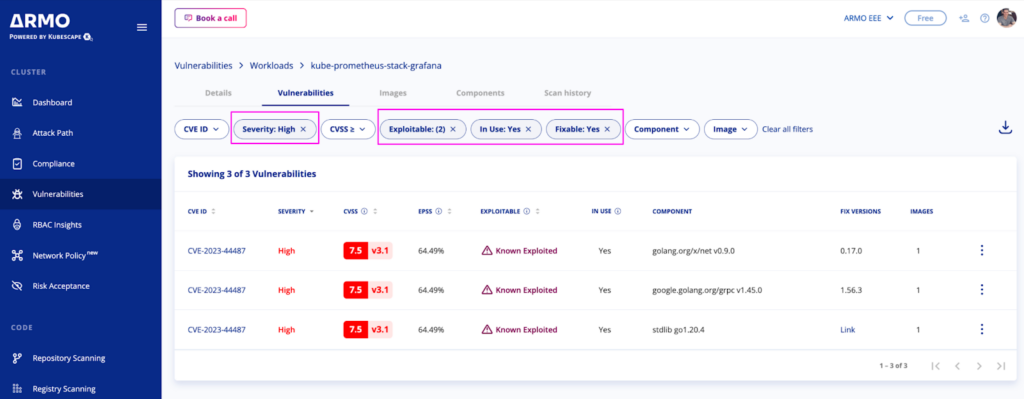
Selecting an exploitable CVE will trigger a side window to appear, which encompasses comprehensive details, such as:
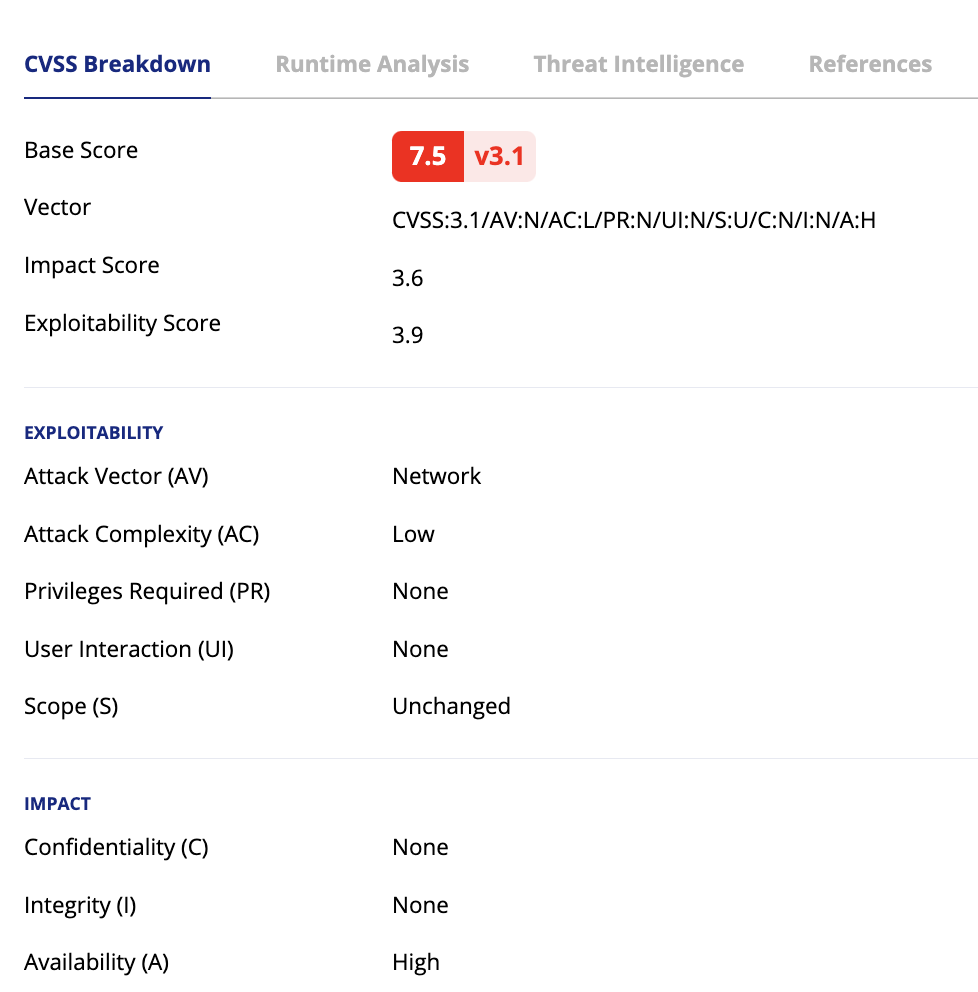
CVSS Breakdown – Is the detailed analysis and categorization of a security vulnerability based on Common Vulnerability Scoring System (CVSS). It assesses factors like severity, exploitability, and impact to provide a comprehensive understanding of the vulnerability’s characteristics. This process helps users gauge the potential risks associated with the vulnerability more effectively.
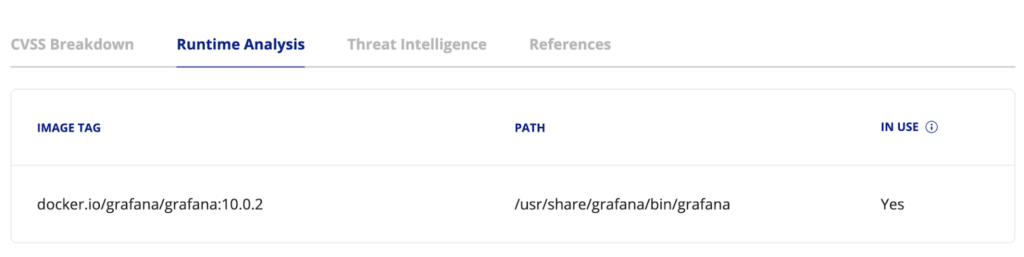
Runtime Analysis – Shows the affected image and indicates whether the vulnerable package is In Use (loaded to the memory)
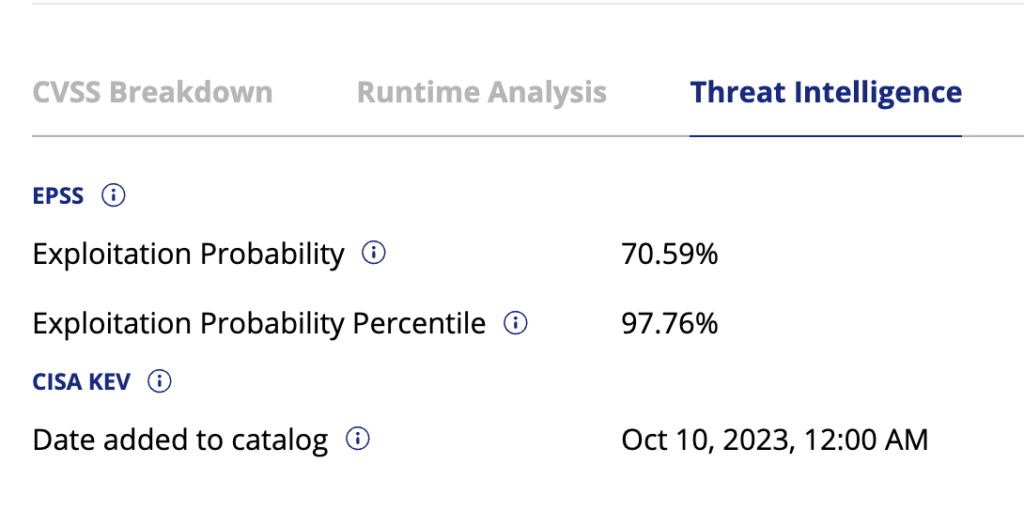
Threat Intelligence – Shows exploitability information from
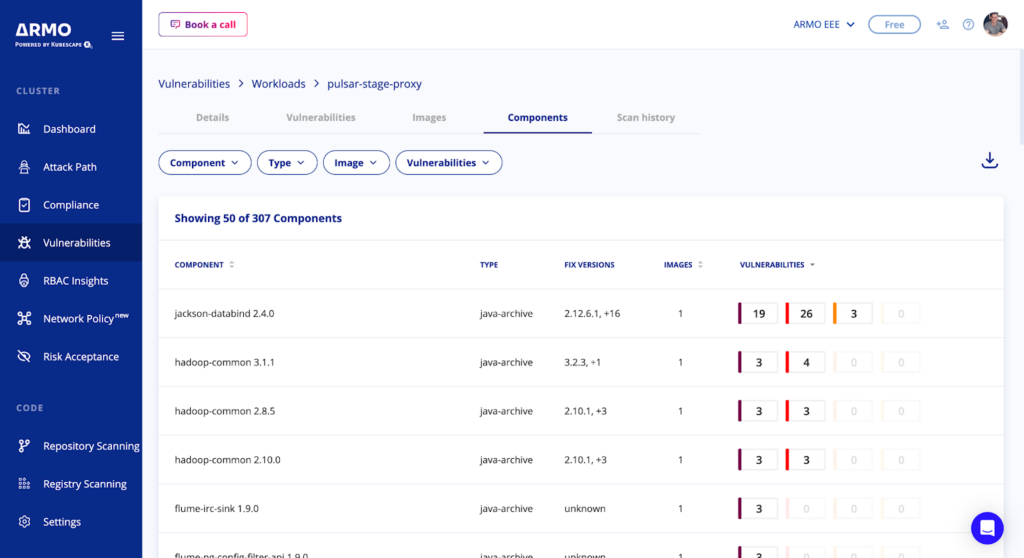
During vulnerability scanning, ARMO Platform checks the active workloads and hosts. It then creates a runtime list of software components for each target called SBOM (Software Bill of Materials). This SBOM is sent to the workload components view for matching vulnerabilities.
When examining the details of a workload there is the possibility to view the components in it, effectively giving a view of the SBOM.
ARMO Platform helps you secure your Kubernetes environments with runtime-based vulnerability management. In this post, you learned about how this is implemented in workloads. Using ARMO Platform, you can see the security status of each workload, including the number and severity of vulnerabilities, the exploitability, and the recommended actions.
However, this is just the beginning. We are working hard to provide you with a comprehensive and user-friendly solution that covers all aspects of Kubernetes vulnerability management. Here is a sneak preview of what is coming soon:
So, stay tuned for our upcoming features.
Implementing Runtime-based vulnerability management and focusing on the most exploitable vulnerabilities hardens Kubernetes environments, preempting potential threats. ARMO Platform’s risk-based vulnerability management simplifies the identification and resolution of critical vulnerabilities. Thus, fostering seamless collaboration between security and development teams. This approach enhances the efficiency and effectiveness of Kubernetes security tasks. Try ARMO Platform today!

The only runtime-driven, open-source first, cloud security platform:
Continuously minimizes cloud attack surface
Secures your registries, clusters and images
Protects your on-prem and cloud workloads

Within 24 hours, three new high-severity vulnerabilities were disclosed in runc, the low-level runtime that...

Hi there,We’ve just dropped a fresh batch of updates to help you cut through the...

These days it seems everyone is obsessed with MCP servers, me included. After studying the...