Known Exploited Vulnerabilities Catalog (KEV)
In cybersecurity, vulnerabilities are weaknesses (actually bugs) that attackers exploit to compromise systems or data. They’re identified by CVEs, but not all are equally urgent. The Known Exploited Vulnerabilities catalog (KEV) helps with prioritization by listing CVEs known to have been actively exploited. This entry explains KEV, how to access it, its information, and its relevance for Kubernetes vulnerability scanning and security.
What is KEV?
The Known Exploited Vulnerabilities catalog (KEV) is a project initiated by the Cybersecurity and Infrastructure Security Agency (CISA) of the U.S. Department of Homeland Security (DHS) in collaboration with the National Institute of Standards and Technology (NIST) and the MITRE Corporation.
The purpose of KEV is to provide a timely and authoritative source of information on CVEs that have been verified to be exploited by malicious actors based on open-source reporting and analysis from various sources, such as security vendors, researchers, media, and government agencies.
KEV is important because it helps security practitioners and decision-makers to focus their attention and resources on the vulnerabilities that pose the most significant risk to their systems and networks and to take the necessary actions to prevent or mitigate potential attacks. Using KEV, users can better understand the threat landscape and the adversary tactics, techniques, and procedures (TTPs) used to exploit known vulnerabilities.
By knowing which vulnerabilities have been actively exploited, users can prioritize them over those that haven’t.
How to Access KEV and How to Use It
KEV is publicly available and can be accessed in different formats, such as web, CSV, and JSON, from the official sources listed below:
- Web: https://us-cert.cisa.gov/kev
- CSV: https://us-cert.cisa.gov/kev.csv
- JSON: https://us-cert.cisa.gov/kev.json
Users can also subscribe to the KEV mailing list to receive notifications of updates and changes to the catalog.
KEV can be used as an input to a vulnerability management prioritization framework, such as the Stakeholder-Specific Vulnerability Categorization (SSVC) model, which is a decision support tool that helps users determine the urgency and importance of patching or mitigating a given vulnerability based on factors such as the value of the asset, the exposure of the vulnerability, the mission impact, and the exploit development and use.
KEV can also be a reference for automated vulnerability and patch management tools that incorporate and flag or prioritize KEV vulnerabilities, such as the NIST National Vulnerability Database (NVD), the MITRE ATT&CK framework, and the Open Vulnerability and Assessment Language (OVAL).
What Information KEV Provides
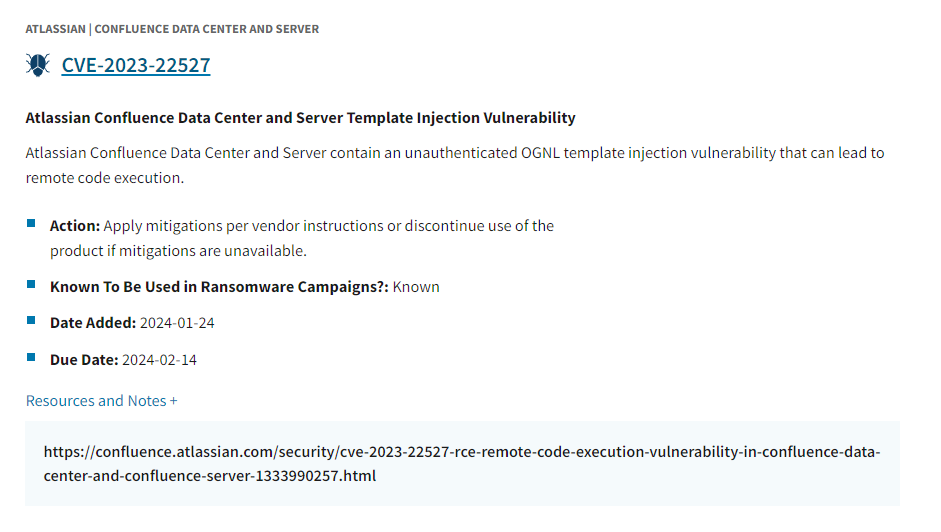
Each entry in the KEV catalog contains the following elements:
- CVE ID: The unique identifier assigned to the vulnerability by the CVE Program is a community-driven effort to standardize and maintain a standard reference for publicly known vulnerabilities.
- Product Name: The name of the software or hardware product affected by the vulnerability, such as Apache Superset, Atlassian, or F5.
- Description: A brief summary of the vulnerability’s nature and impact, such as remote code execution, denial-of-service, or information disclosure.
- Action: The recommended action to be taken by the users to address the vulnerability, such as applying a patch, updating to a newer version, disabling a feature, or following a workaround.
- Status: The vulnerability’s current status, such as Active, Resolved, or Deprecated, indicates whether it is still being exploited, has been fixed or mitigated, or has been removed from the catalog for some reason.
- Date Added: The date when the vulnerability was added to the KEV catalog in YYYY-MM-DD format.
- Due Date: The date the users are advised to take the recommended action to address the vulnerability in YYYY-MM-DD format.
- Resources and Notes: A list of links to additional information and sources on the vulnerability, such as advisories, alerts, reports, blogs, and podcasts, as well as any notes or comments from the KEV team.
An example of a KEV entry is shown below:
How is KEV relevant for Kubernetes security?
Kubernetes is an open-source platform for automating containerized applications’ deployment, scaling, and management. Developers and organizations use Kubernetes to run their applications in the cloud or on-premises, as it offers many benefits, such as high availability, scalability, portability, and flexibility.
However, Kubernetes also introduces new challenges and risks for K8s security, as it exposes a large and dynamic attack surface and requires complex configurations and integrations with various components and services.
Users can use the KEV catalog to identify and prioritize the most critical and prevalent vulnerabilities that affect their Kubernetes clusters, such as those related to the Kubernetes API server, kubelet, container runtime, the network plugins, the storage drivers, the ingress controllers, the service meshes, or the application dependencies. Using KEV, users can gain insight into the real-world exploitation of these vulnerabilities and their potential impact on their Kubernetes environments.
Some tips and best practices for vulnerability management in Kubernetes are:
- Use KEV to identify the vulnerabilities exploited in the wild and require immediate attention.
- Apply the principle of least privilege to your systems and networks, which minimizes the attack surface and the opportunities for lateral movement.
- Apply patches or updates to the Kubernetes components and dependencies as soon as they are available, and follow the official release notes and changelogs for any breaking changes or compatibility issues.
- Disable or remove any features or components that are not needed or used, such as alpha or beta features, deprecated APIs, or unused ports or protocols, to reduce the attack surface and the exposure of the vulnerabilities.
- Comply with the industry standards and regulations for Kubernetes security, such as the Center for Internet Security (CIS) Kubernetes Benchmark, the National Institute of Standards and Technology (NIST) Application Container Security Guide, or the Payment Card Industry Data Security Standard (PCI DSS).
- Scan and monitor the Kubernetes clusters and the container images for vulnerabilities using automated tools, such as the Kubernetes Security Audit, the Anchore Engine, and Kubescape.
- Enforce security policies and controls using tools that implement the Open Policy Agent (OPA) framework, such as Gatekeeper, Styra DAS, Kubescape or other OPA-based tools.
It is important to note that KEV is not as comprehensive as other CVE databases. Its upside is that the CVEs in KEV are known to have been exploited, so they are important for sure. Having said that it shouldn’t be the only place to look for identifying CVEs. Users should also consult additional vulnerability databases as well as other sources of vulnerability information, such as the Kubernetes Security Announcements, the Kubernetes GitHub Issues, or the Kubernetes Slack Channels, and stay updated on the latest security news and trends.
Enhancing Security
The Known Exploited Vulnerabilities catalog is a valuable resource for security professionals and organizations that must prioritize and mitigate the vulnerabilities actively exploited by attackers. KEV provides a curated list of CVEs confirmed to be exploited in the wild, along with relevant information and guidance on addressing them.
KEV is especially relevant for Kubernetes security, as it helps users identify and protect their Kubernetes clusters from the most critical and prevalent vulnerabilities that affect the Kubernetes components and dependencies. Users can improve their security posture and resilience and reduce the risk of compromise and data breaches.