The Kubernetes network policies you need today
In the dynamic world of Kubernetes, container orchestration is just the tip of the iceberg....

In the dynamic world of Kubernetes, container orchestration is just the tip of the iceberg....
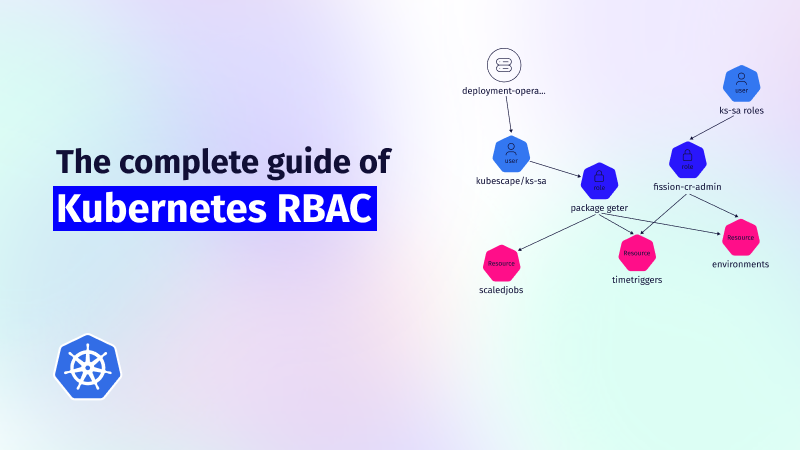
This guide explores the challenges of RBAC implementation, best practices for managing RBAC in Kubernetes,...

In the evolving landscape of technology, cloud agnosticism has seen increasing traction. This refers to...

Kubernetes is an open-source platform for governing clusters of containerized application services. Kubernetes automates the...

Kubernetes is a container orchestration tool that helps with the deployment and management of containers....

I had always wanted to use sidecars with Istio or Splunk forwarder in production, but...
Kubernetes has become one of the most popular platforms for running cloud-native applications. This popularity...

This post compares popular Kubernetes security and compliance frameworks, how they differ, when to use...

Improve Kubernetes compliance with ARMO Platform's user-friendly Compliance Score for enhanced security. Click here to...

This post discusses the five Trust Services Criteria (TSC) of SOC 2 and how they...

This post highlights the importance of securing Kubernetes for HIPAA compliance, utilizing tools such as...

This post explores the topic of Kubernetes compliance under ISO 27001, which is one of...