The vulnerability puzzle: understanding base images and their relationship to CVEs
Have you ever heard of CVEs? Maybe not by their acronym, but Common Vulnerabilities and...
Dec 12, 2021
On Dec 9th, a critical zero-day vulnerability – CVE-2021-44228 – was announced concerning the Java logging framework – Log4j
All current versions of log4j2 up to 2.14.1 are vulnerable. To remediate this vulnerability, please update to version 2.15.0 or later.
Kubernetes is written in GO so it is not directly affected, but applications running in Kubernetes can be vulnerable, and if exploited, can be used to spread laterally and attack Kubernetes itself.
Kubernetes clusters running Java workloads are most likely using the Log4j logging framework and are at high risk of being exposed to this vulnerability.
Since this is an RCE-type vulnerability, the impact is critical as the attacker may have direct network access to vulnerable microservices. Kubernetes ingress resources are usually configured to have wide access to other in-cluster components as they redirect external APIs to corresponding internal microservices.
Are your Kubernetes’ clusters exposed?
The new Kubescape image scanner detects if this vulnerability exists in a Kubernetes cluster. The remediation and best practices according to the test results are also documented.
Kubescape users can simply run the Kubescape latest version and get the results immediately.
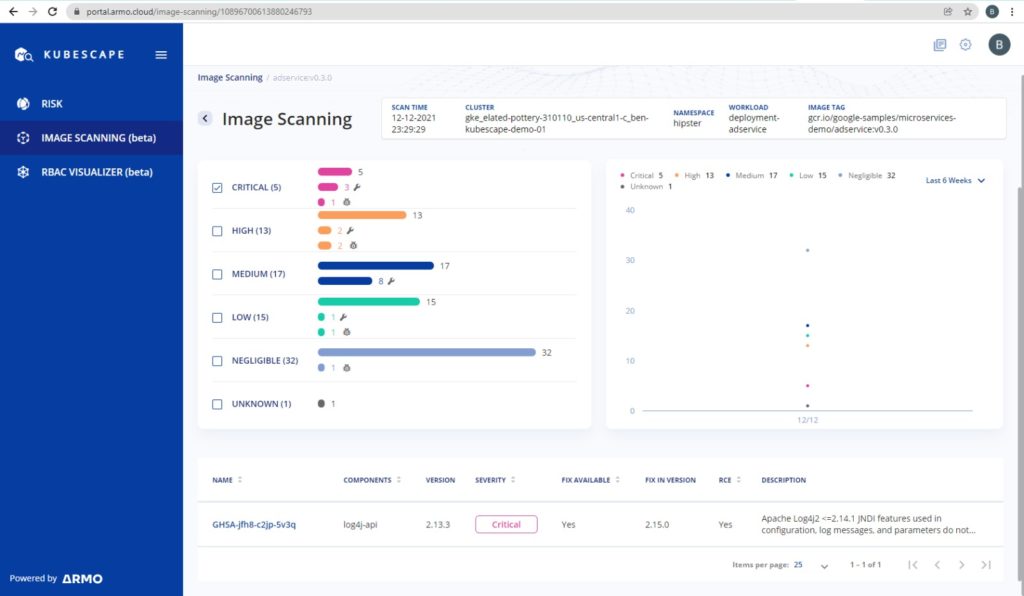
The image scanner detects the vulnerable versions of Log4j2 JAR files on your container image and marks them as “CVE-2021-44228” or “GHSA-jfh8-c2jp-5v3q” depending on the vulnerability database version.
Kubescape users – Please make sure to update to the latest Kubescape version in GitHub, or through the following command:
curl -s https://raw.githubusercontent.com/armosec/kubescape/master/install.sh | /bin/bash
Not a Kubescape user? Please sign-up for free here, install the Kubescape image scanner and check your cluster in just a few minutes To learn more – see details at ARMO-HUB.
Click here to learn more about Kubernetes security best practices
Have you ever heard of CVEs? Maybe not by their acronym, but Common Vulnerabilities and...

A series of critical vulnerabilities has been uncovered in the Common Unix Printing System (CUPS),...

Introduction Attention: a new Kubernetes vulnerability was uncovered by André Storfjord Kristiansen (@dev-bio on GitHub)...